What is the Chain of Custody? - Definition, Procedures & Importance - Video & Lesson Transcript | Study.com

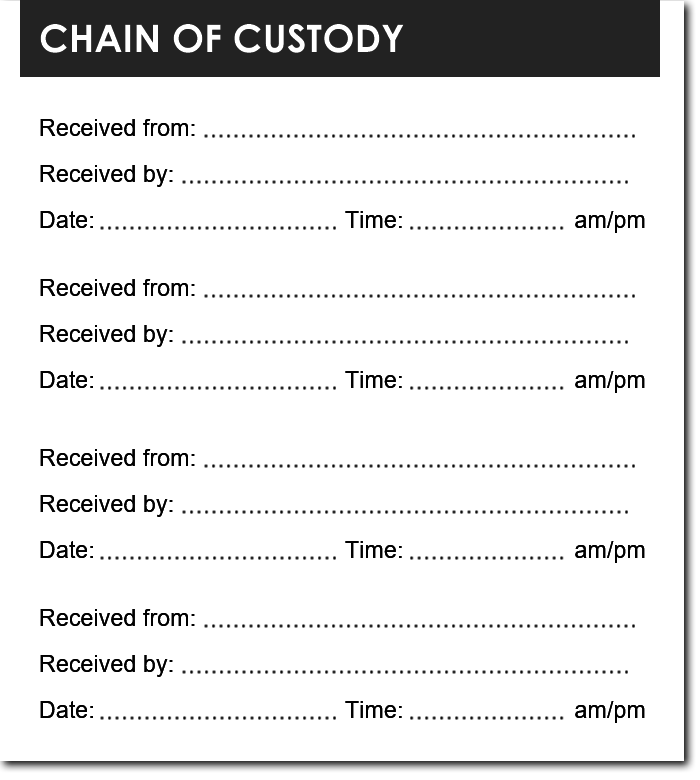
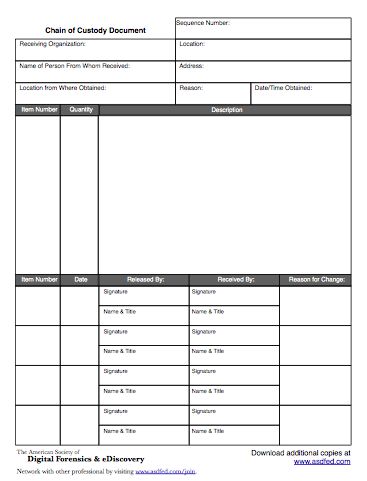
Kenya CyberSecurity & Forensics Association: KCSFA on Twitter: "Chain of Custody Form To implement chain of Custody a Chain of Custody Form is used to records all the activities pertaining a particular
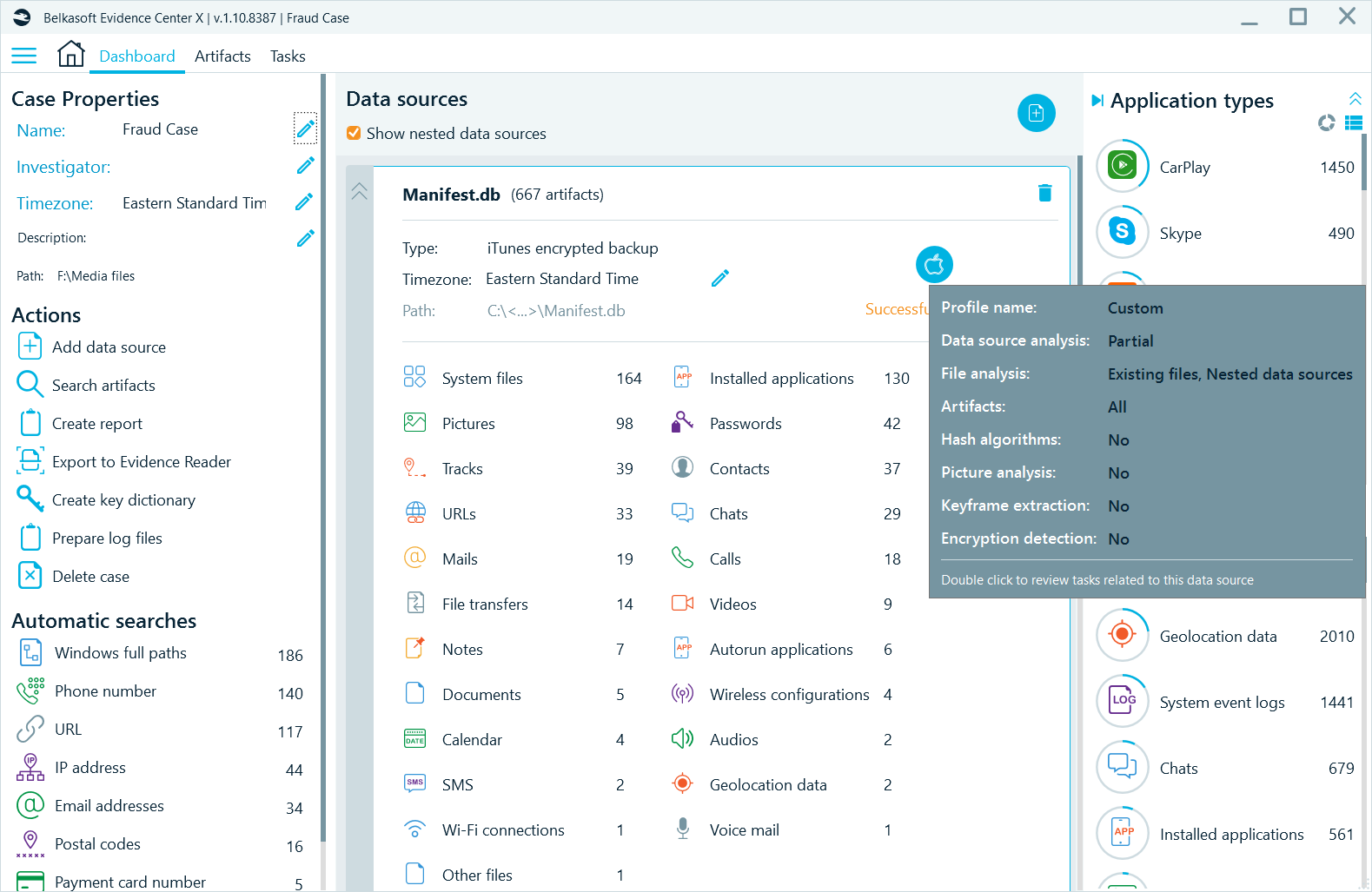
Computer Forensics Chain Of Custody Ppt Powerpoint Presentation Portfolio Graphic | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
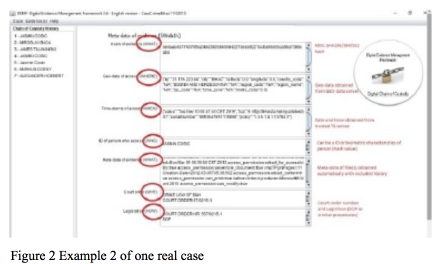
![PDF] Digital Chain of Custody: State of the Art | Semantic Scholar PDF] Digital Chain of Custody: State of the Art | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9e8a1f74a9dc68ce2f475c42fb42f47f3d7a955e/3-Figure1-1.png)
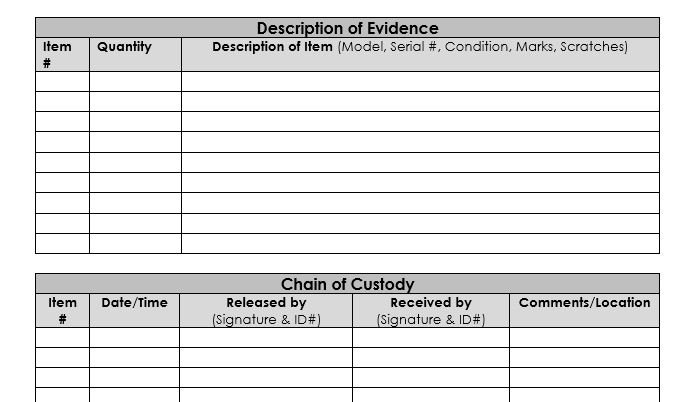


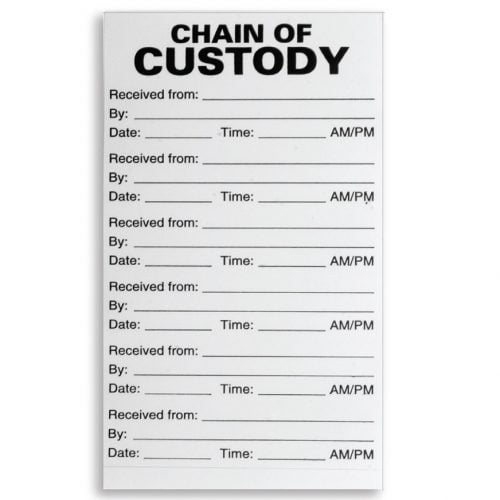
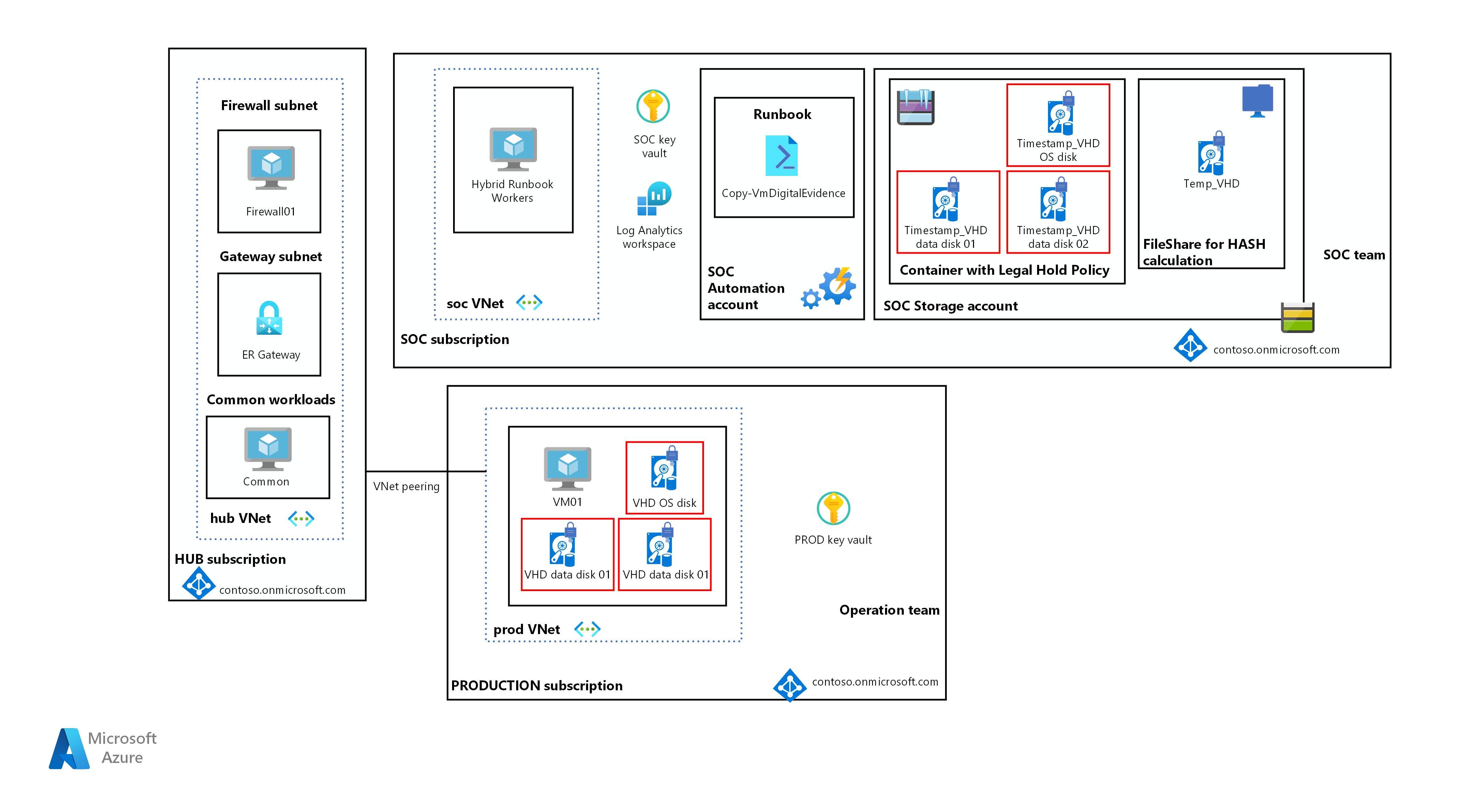





![PDF] Digital Chain of Custody: State of the Art | Semantic Scholar PDF] Digital Chain of Custody: State of the Art | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9e8a1f74a9dc68ce2f475c42fb42f47f3d7a955e/3-Figure2-1.png)