Security Goals in cryptography | Confidentiality | Integrity | Availability | Authentication - YouTube

User Authentication & Authorization in Express: Introduction: User Authentication & Authorization in Express Cheatsheet | Codecademy

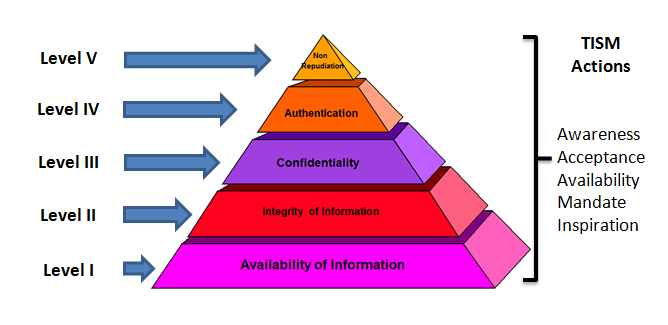
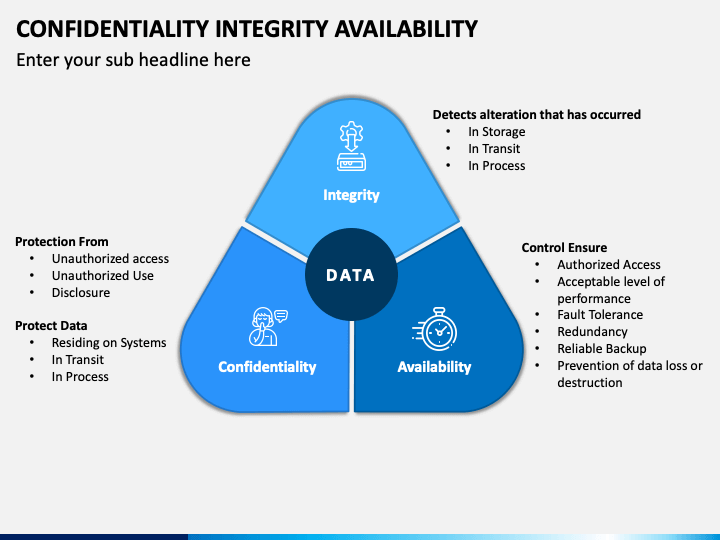
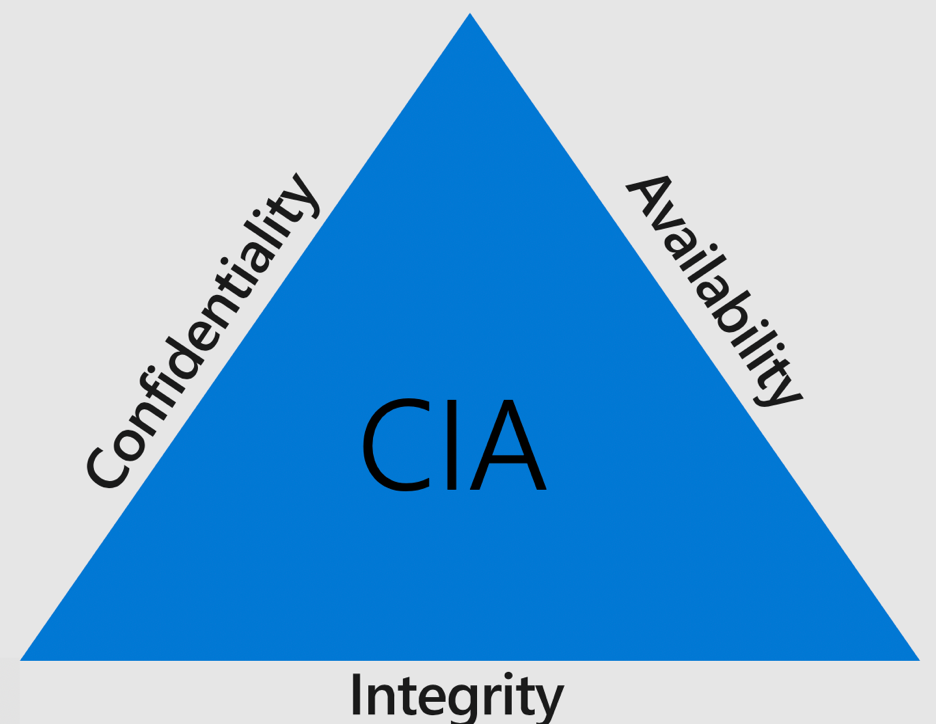
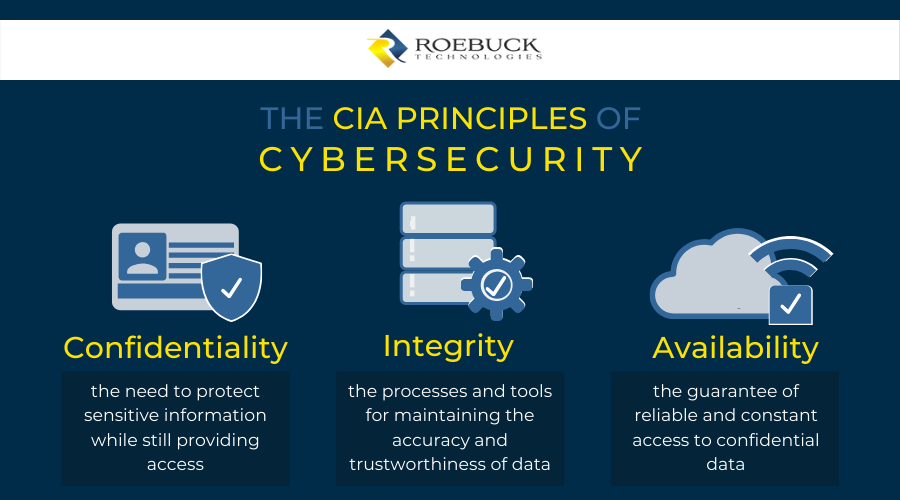
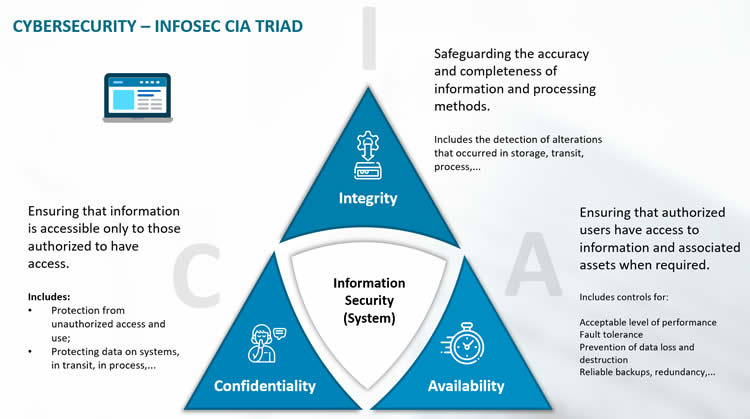
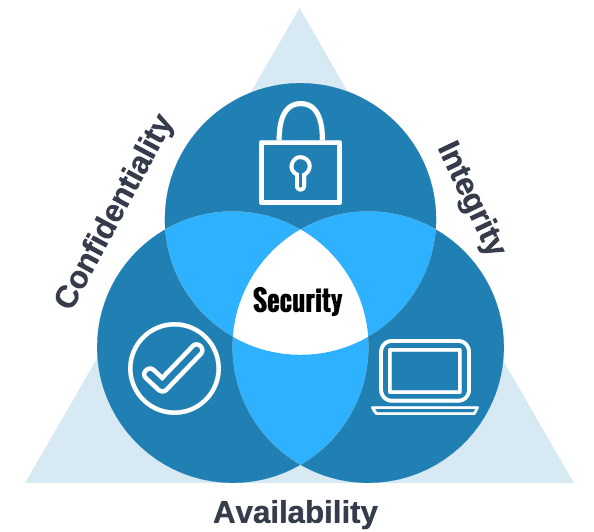
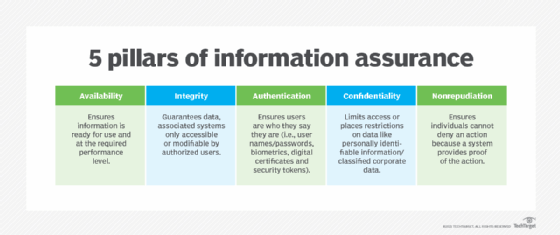
Introduction to cybersecurite - Confidentiality, Integrity, and Availability Confidentiality, integrity and availability, known as the CIA triad (Figure 1), is a guideline for information security for an organization. Confidentiality ensures the privacy
Scheme 3-Authenticity, Confidentiality, Non-repudiation, and Integrity. | Download Scientific Diagram

CN8816: Network Security1 Confidentiality, Integrity & Authentication Confidentiality - Symmetric Key Encryption Data Integrity – MD-5, SHA and HMAC Public/Private. - ppt download

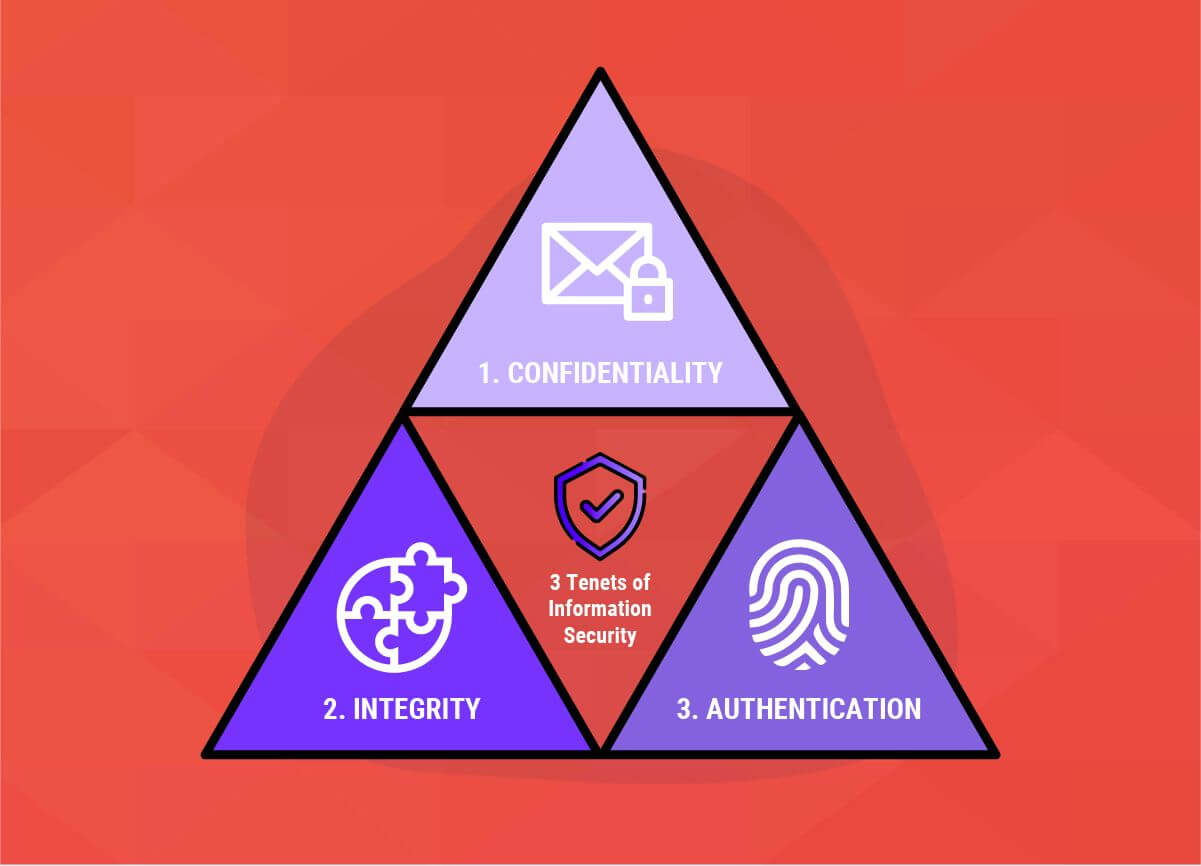
EC-Council - The STRIDE methodology aims to ensure that an application meets the security directives of the CIA triad (Confidentiality, Integrity, and Availability), alongside Authentication, Authorization, and Non-Repudiation. Security professionals ...
WCF | Confidentiality Integrity Authentication Authorization Transport Level Message Level Security In WCF | knowsh.com

Data Confidentiality, Integrity, and Authentication: Computer Science & IT Book Chapter | IGI Global

What Is the CIA Security Triad? Confidentiality, Integrity, Availability Explained – BMC Software | Blogs