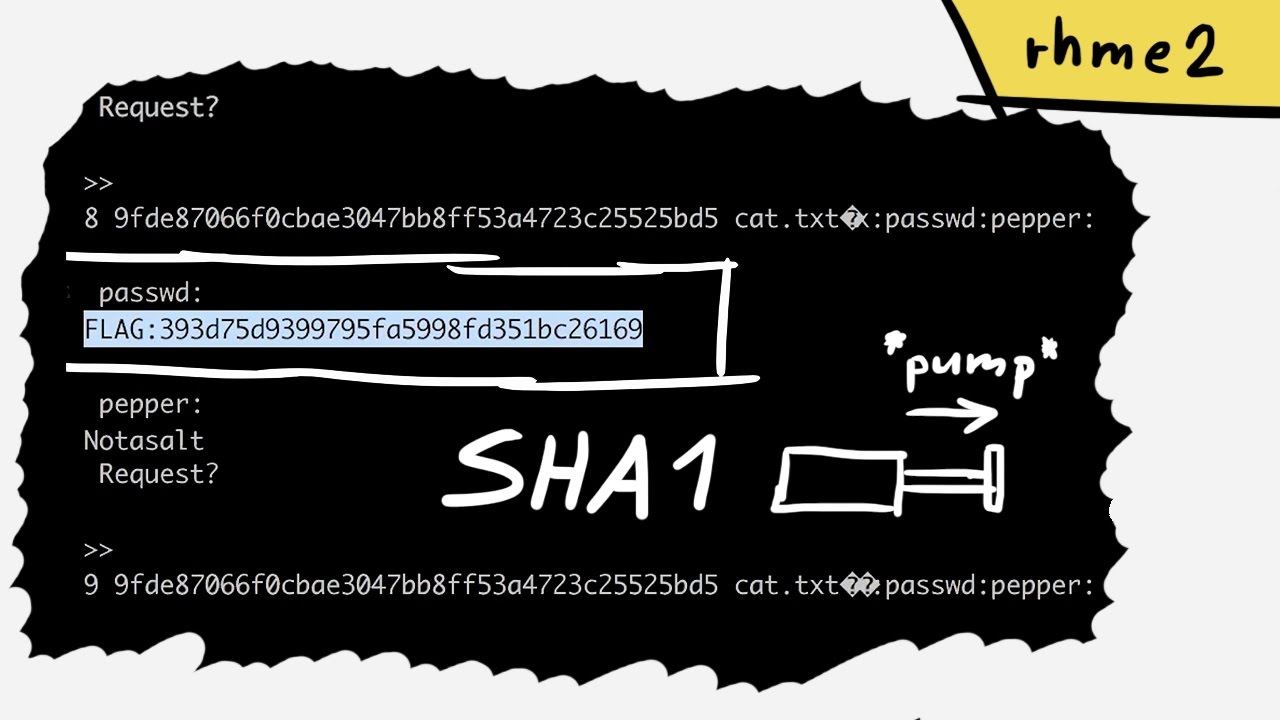
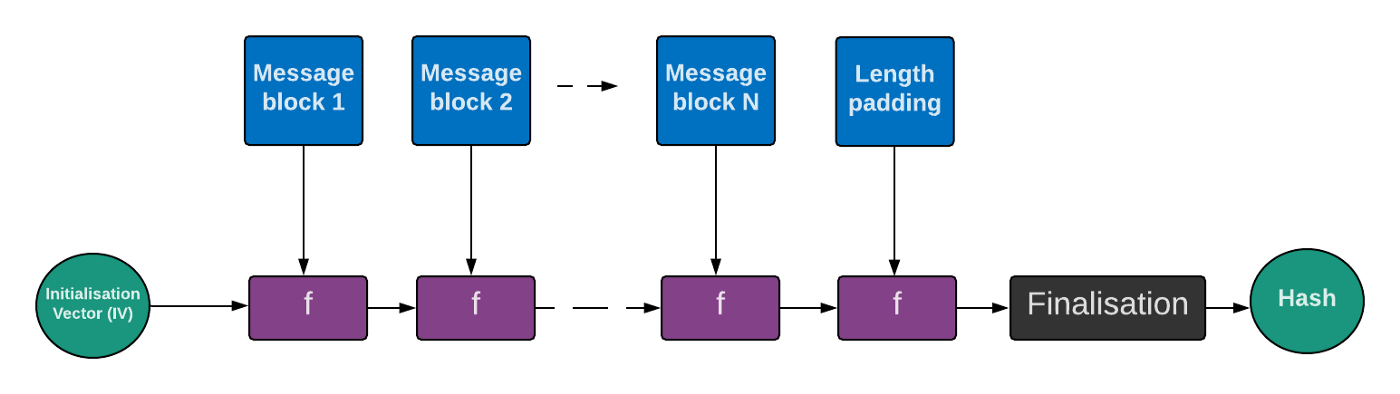
hash - Why HAIFA and sponge constructions are not prone to length extension attacks? - Cryptography Stack Exchange

Table 1 from Why narrow-pipe cryptographic hash functions are not a match to wide-pipe cryptographic hash functions ? | Semantic Scholar
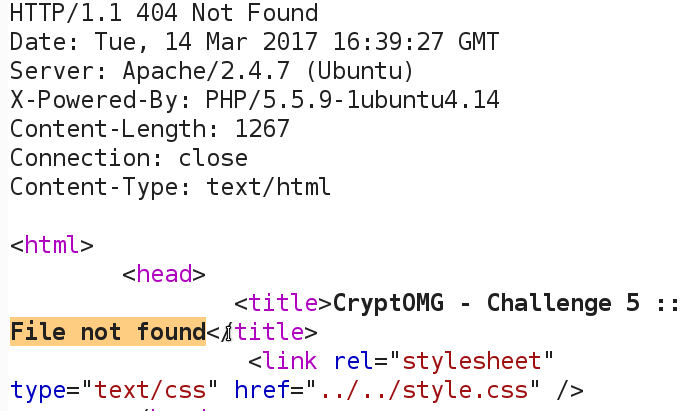
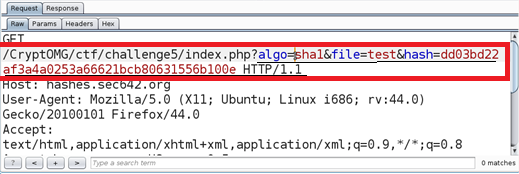
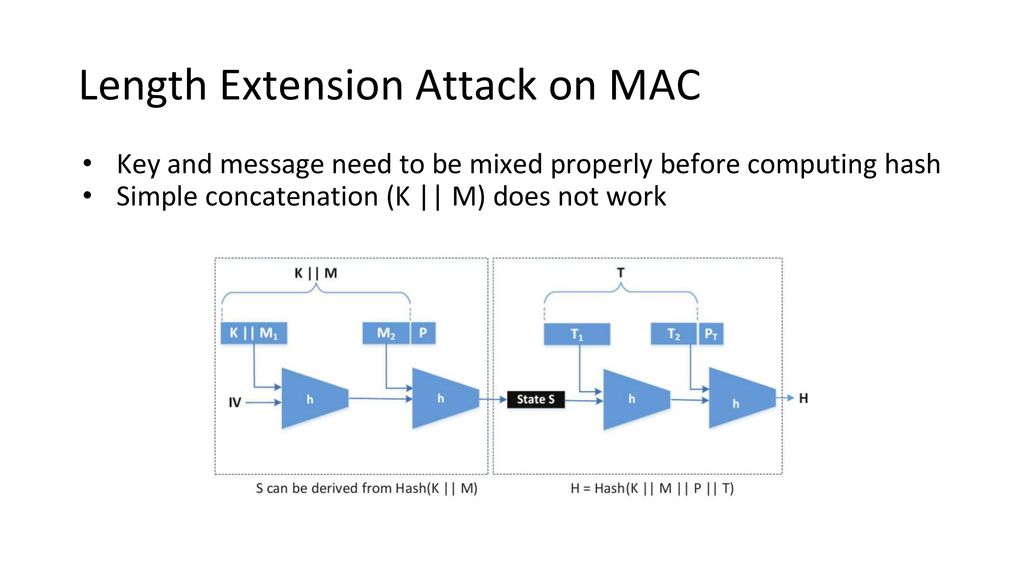
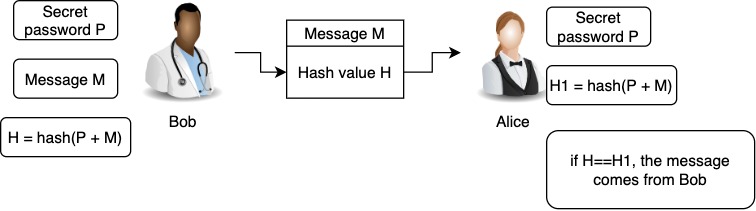
SANS Penetration Testing | Modern Web Application Penetration Testing Part 2, Hash Length Extension Attacks | SANS Institute
HashPump - Exploit Hash Length Extension Attack - Darknet - Hacking Tools, Hacker News & Cyber Security
GitHub - aabdelw1/length-extension-attack: a deeper dive into exploiting the SHA-1 hashing algorithm