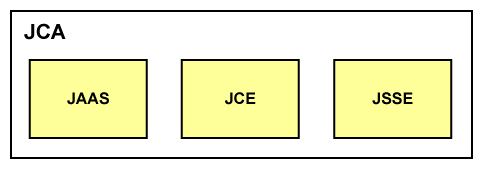
Architecture and extensible security elements of the Java platform.... | Download Scientific Diagram

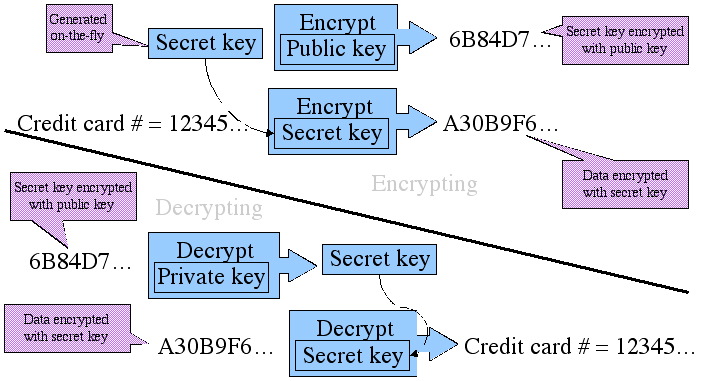
Java Cryptography Extensions architectural model with unconditional... | Download Scientific Diagram

Java Cryptography Extensions architectural model with unconditional... | Download Scientific Diagram
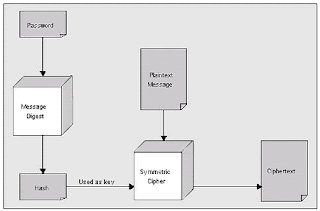
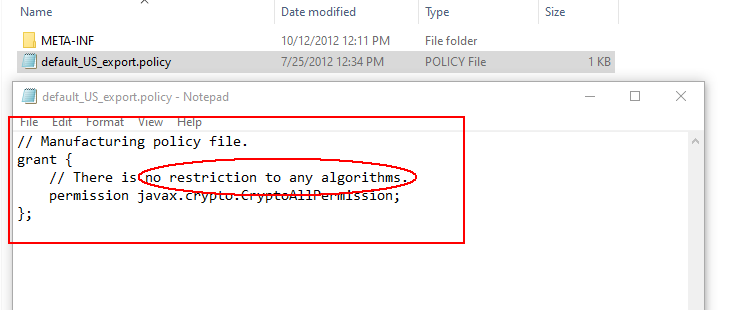
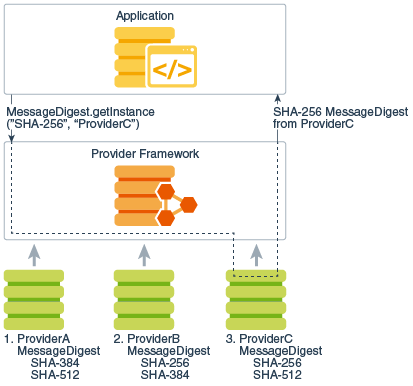
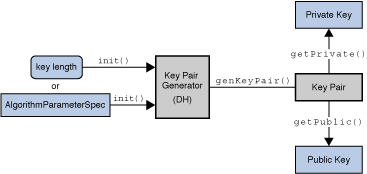
Identity and Access Management: How Java Cryptography Extension works - Password Based encryption Concept

Java Cryptography Extensions architectural model with unconditional... | Download Scientific Diagram