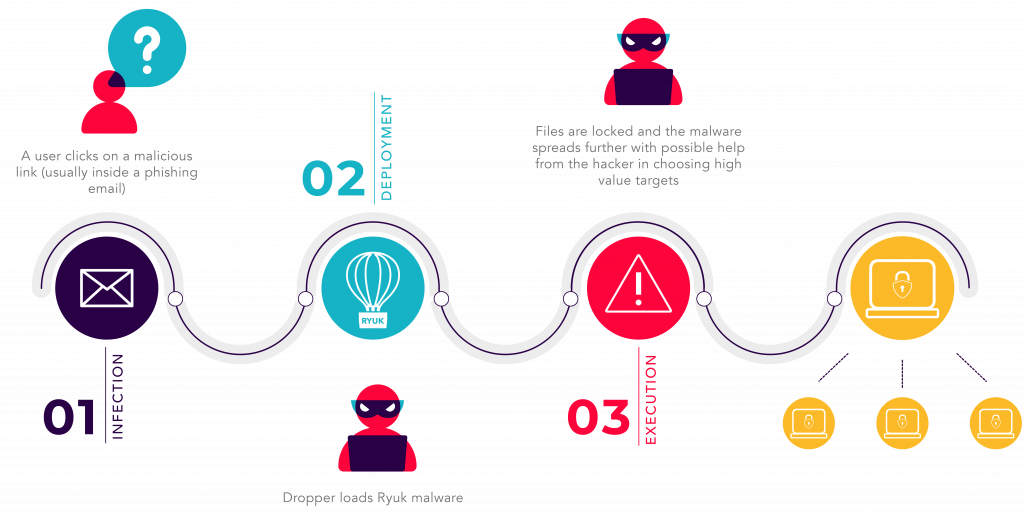
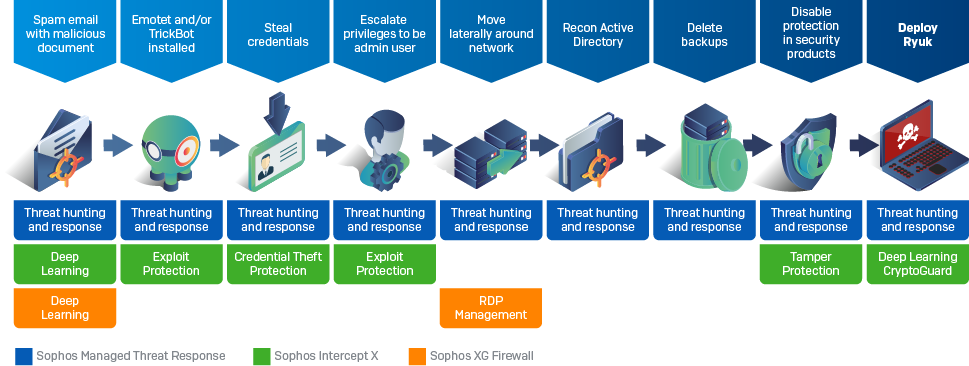
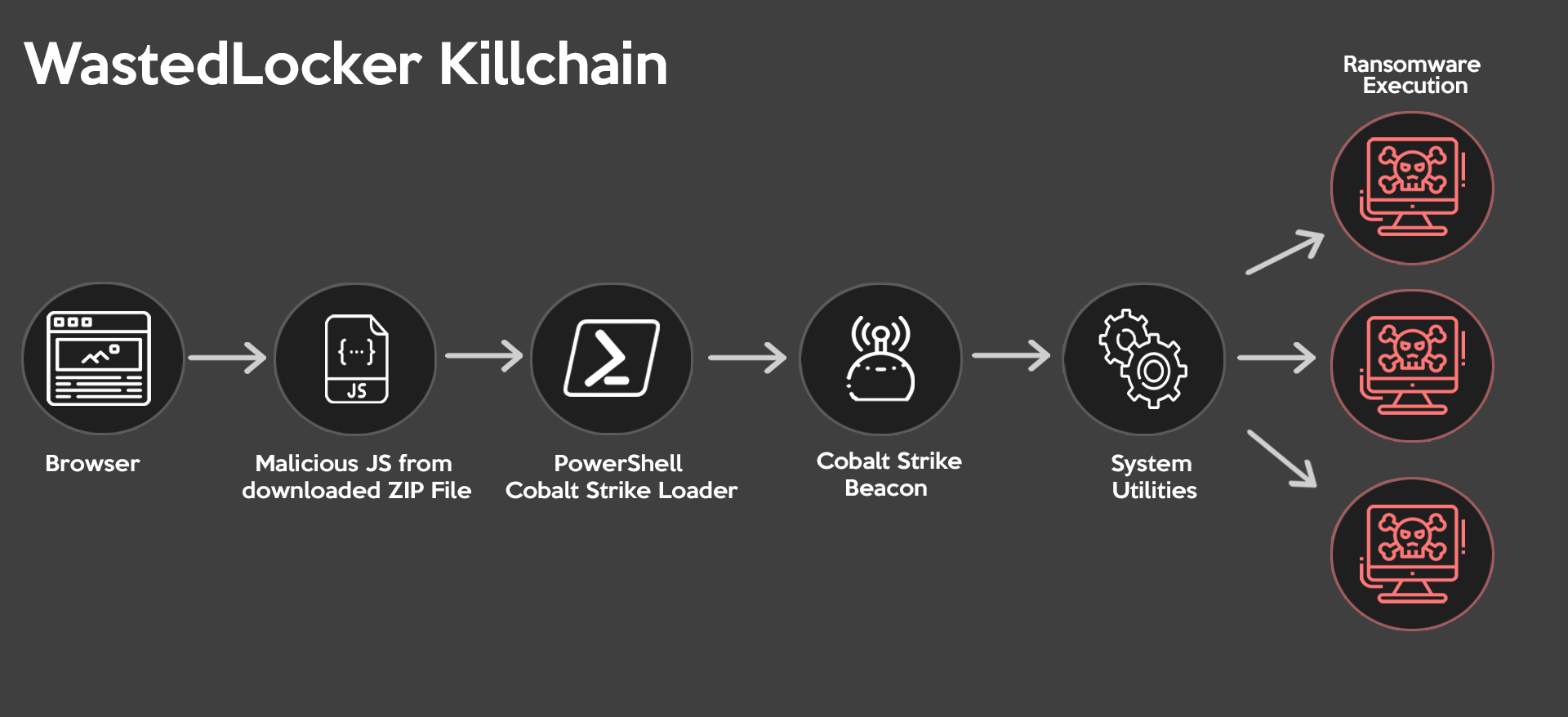
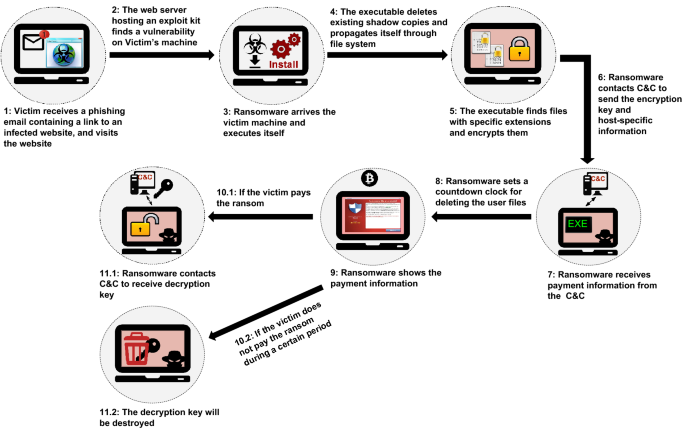
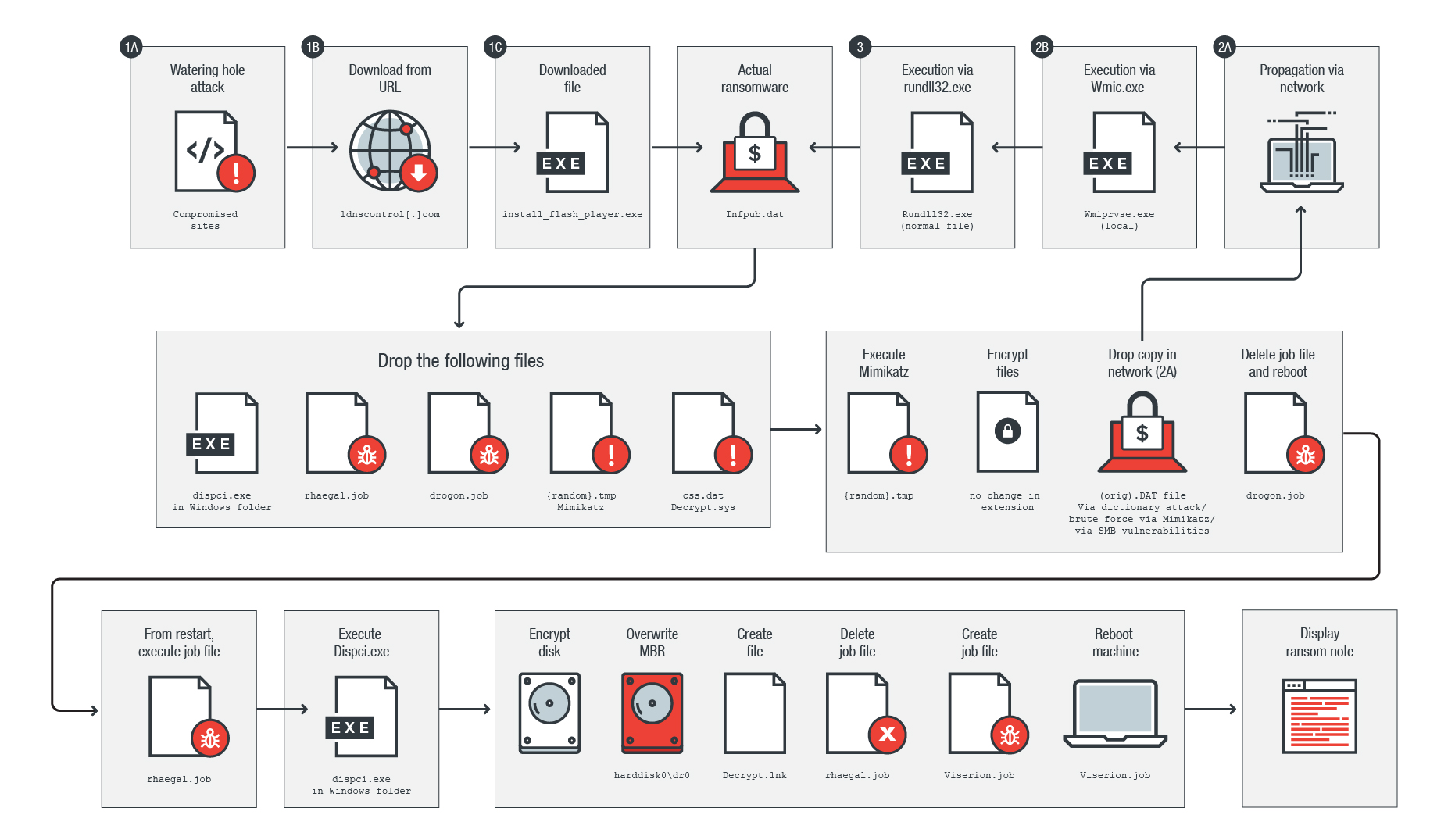
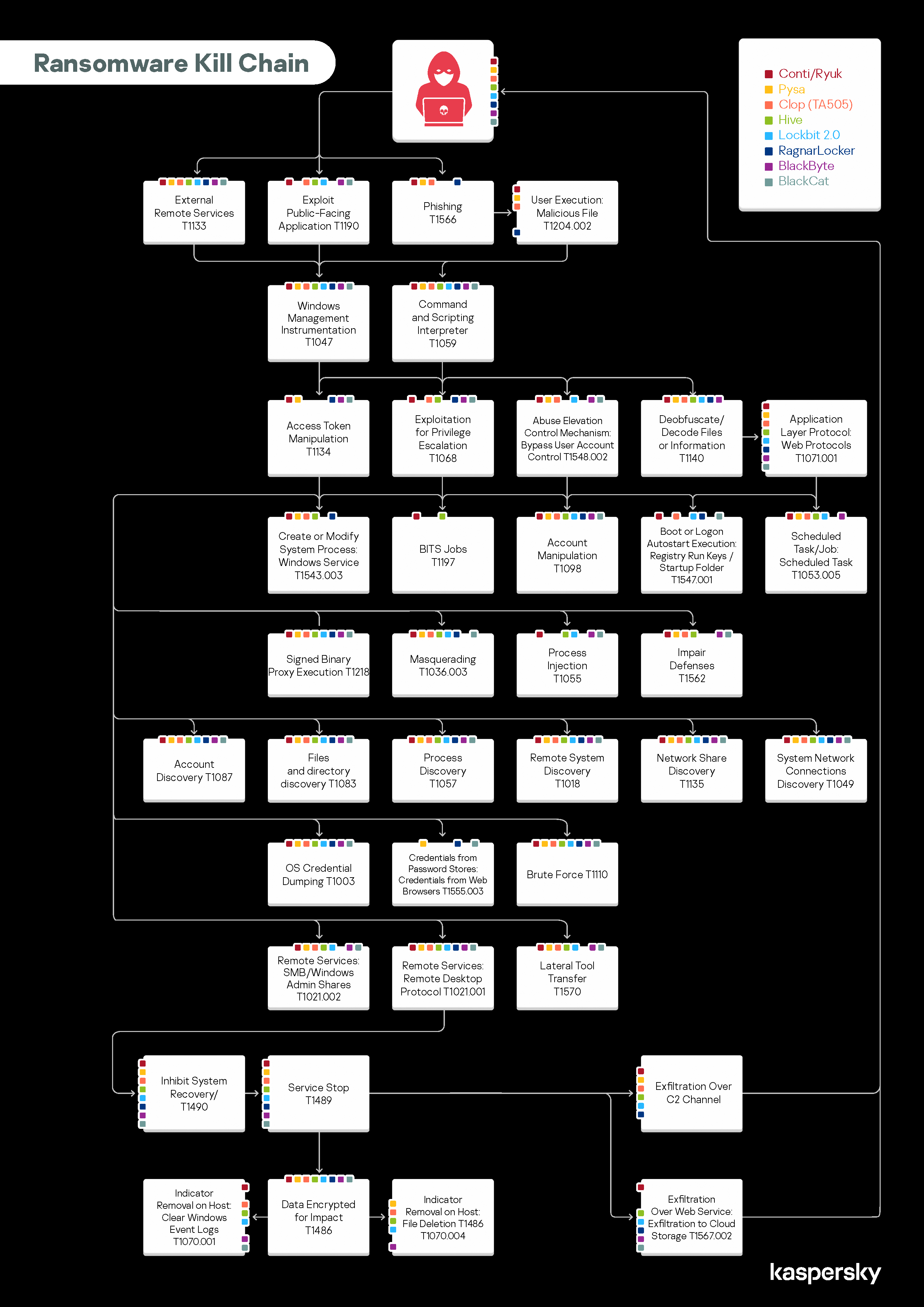
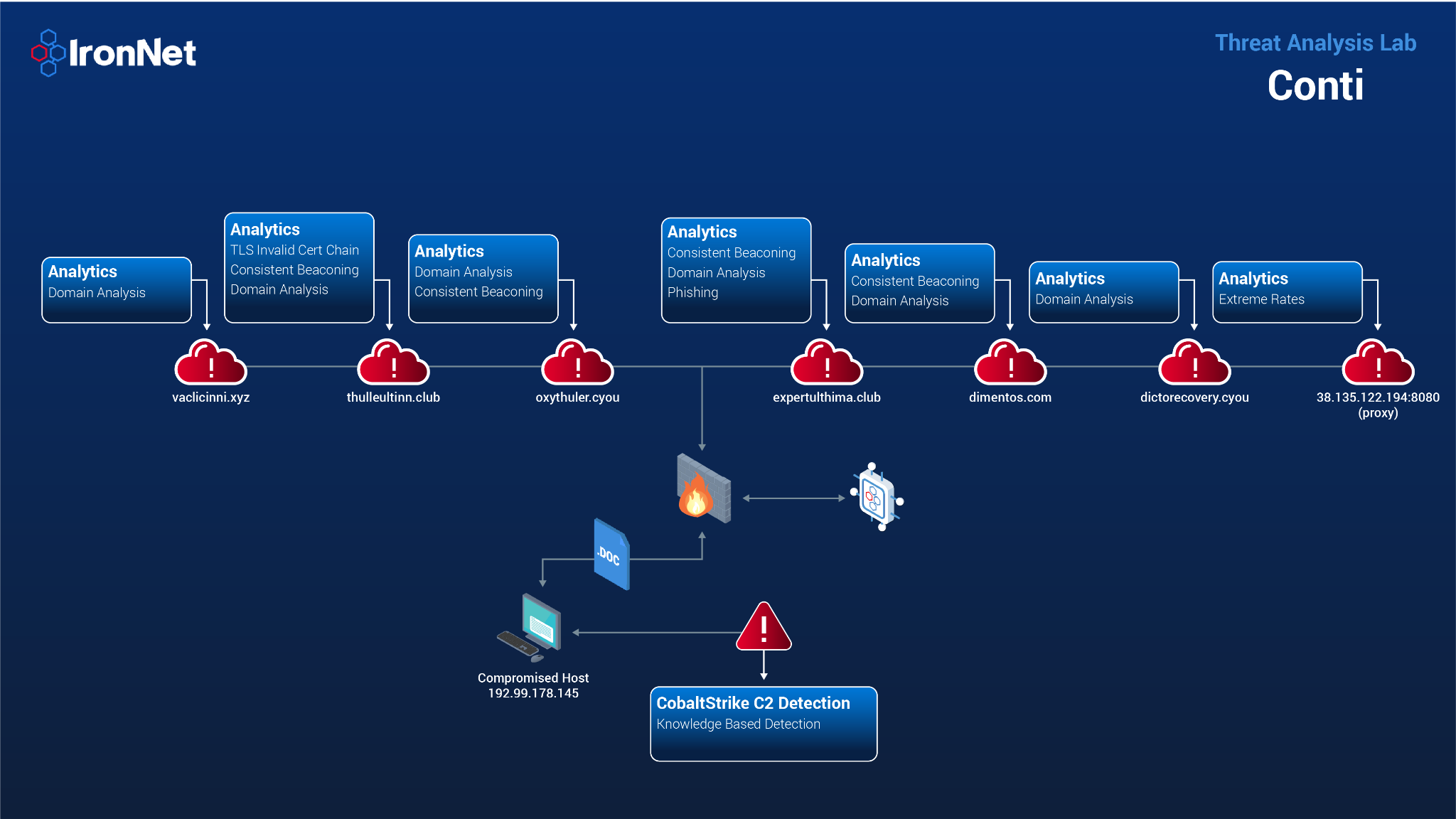
NoGoFallMaga on Twitter: "3/ Our speaker then drew our attention to the ransomware kill chain which is how bad actors make use of ransomware He then talked about the 3 stages of
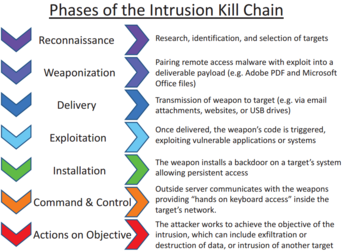
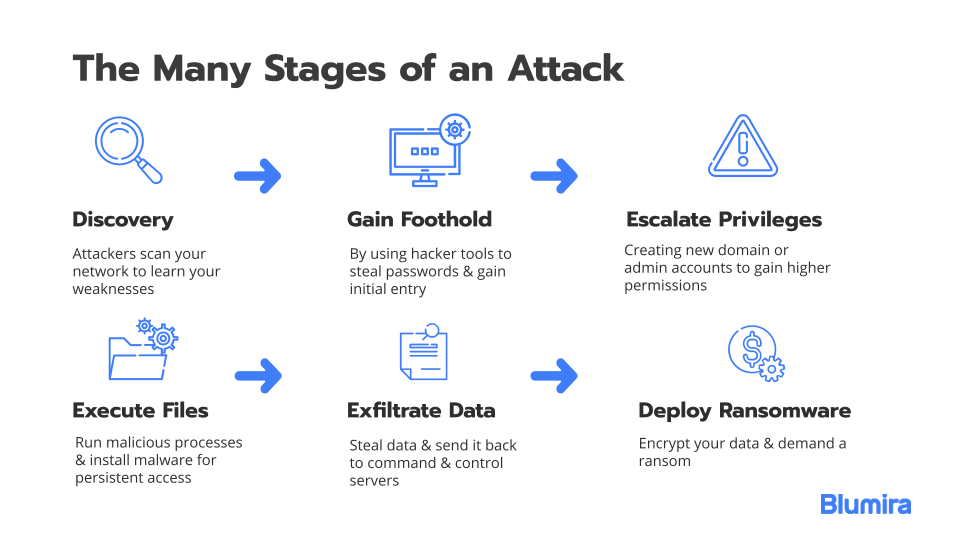
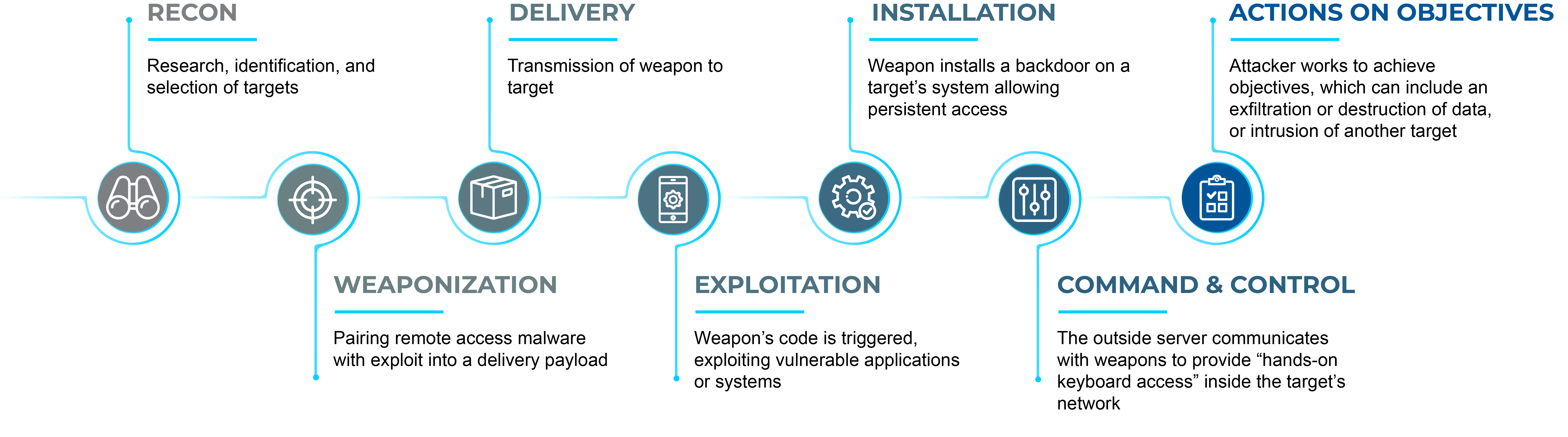
![Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram](https://www.researchgate.net/publication/335024682/figure/fig1/AS:789313017098241@1565198296990/Lockheed-Martin-Cyber-Kill-Chain-CKC-22-seven-steps-The-part-that-is-specified-with.png)
Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram

I2CE3: A dedicated and separated attack chain for ransomware offenses as the most infamous cyber extortion - ScienceDirect

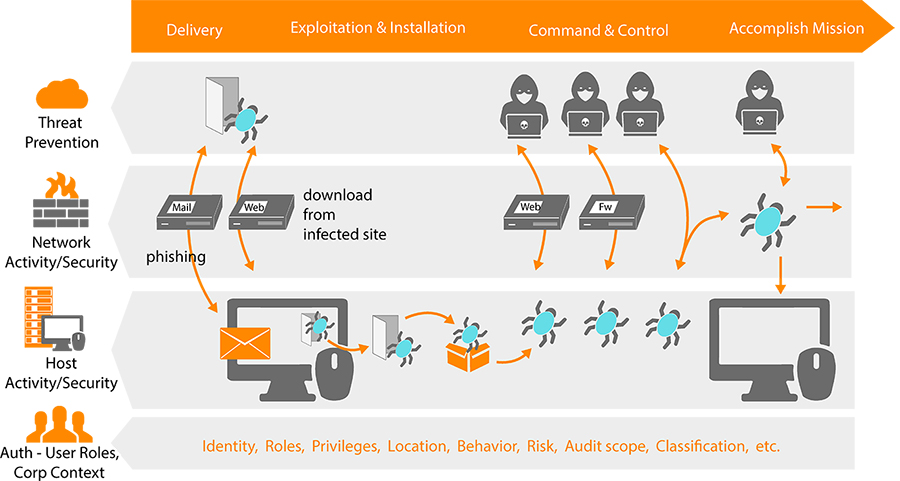
Cyber Startup Observatory on Twitter: "The Ransomware Kill Chain Available for download in Press Quality: https://t.co/2ctw6MLUnq For further information on cyber topics & innovation: https://t.co/PRz5R1HD6M #CyberSecurity #InfoSec ...


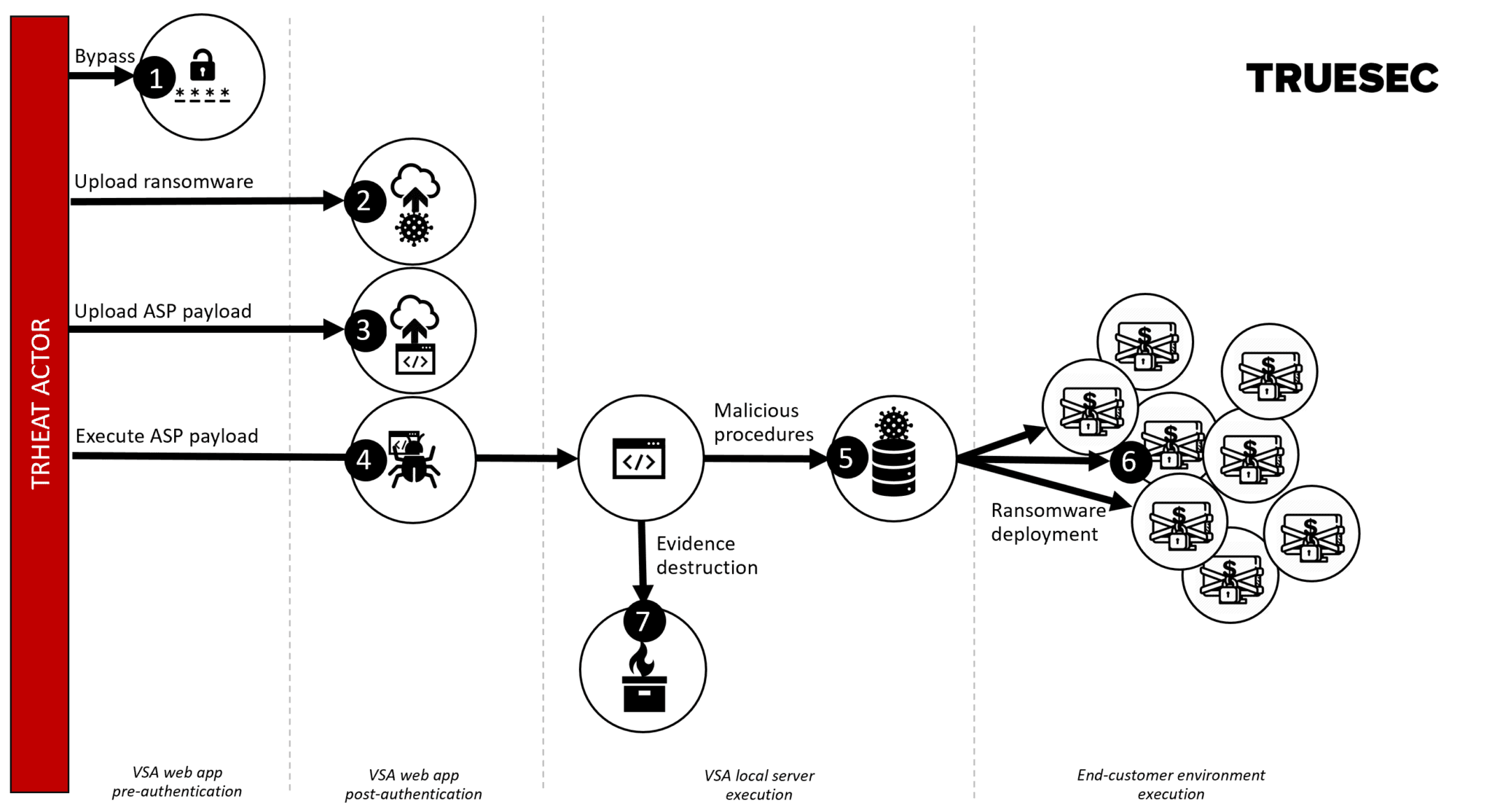
![What is Maze Ransomware? [Technical Analysis] | CrowdStrike What is Maze Ransomware? [Technical Analysis] | CrowdStrike](https://www.crowdstrike.com/wp-content/uploads/2020/12/Preempt-Maze-blog-image.png)