![PDF] Using PTES and open-source tools as a way to conduct external footprinting security assessments for intelligence gathering | Semantic Scholar PDF] Using PTES and open-source tools as a way to conduct external footprinting security assessments for intelligence gathering | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6a3111ac894c1b2a2ac312efc4092d00f5f8585a/2-Figure1-1.png)
PDF] Using PTES and open-source tools as a way to conduct external footprinting security assessments for intelligence gathering | Semantic Scholar
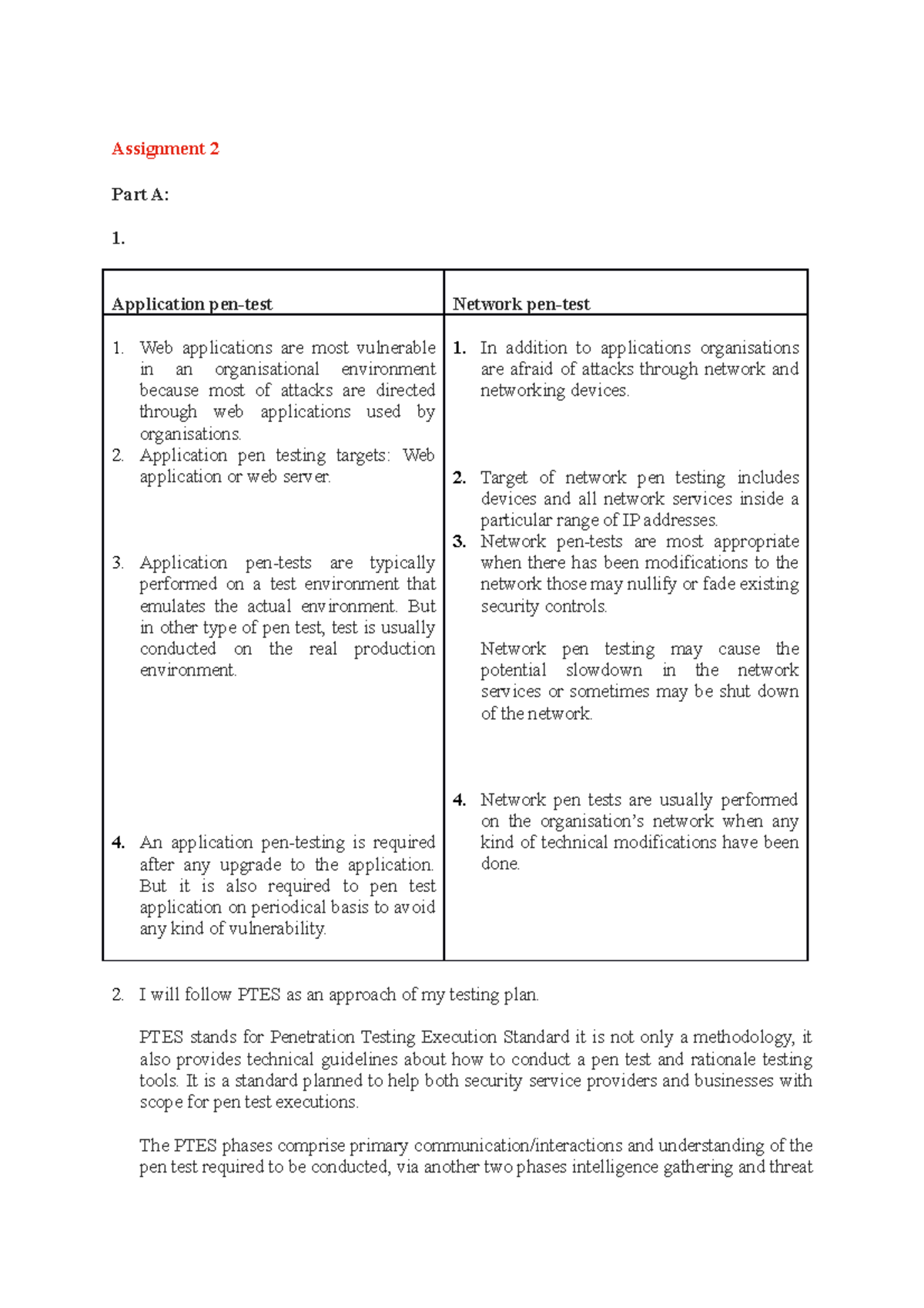
Assignment 2 - Assessment - Assignment 2 Part A: Application pen-test Network pen-test Web - Studocu

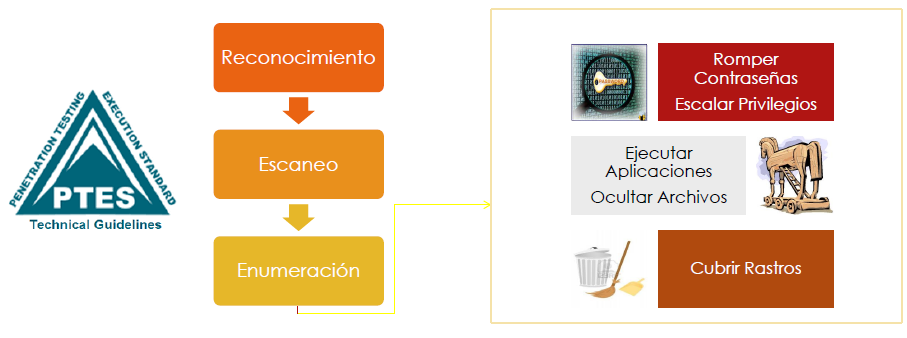
PTES Technical Guidelines - The Penetration Testing Execution Standard.pdf - 6/10/2017 PTES Technical Guidelines - The Penetration Testing Execution | Course Hero



















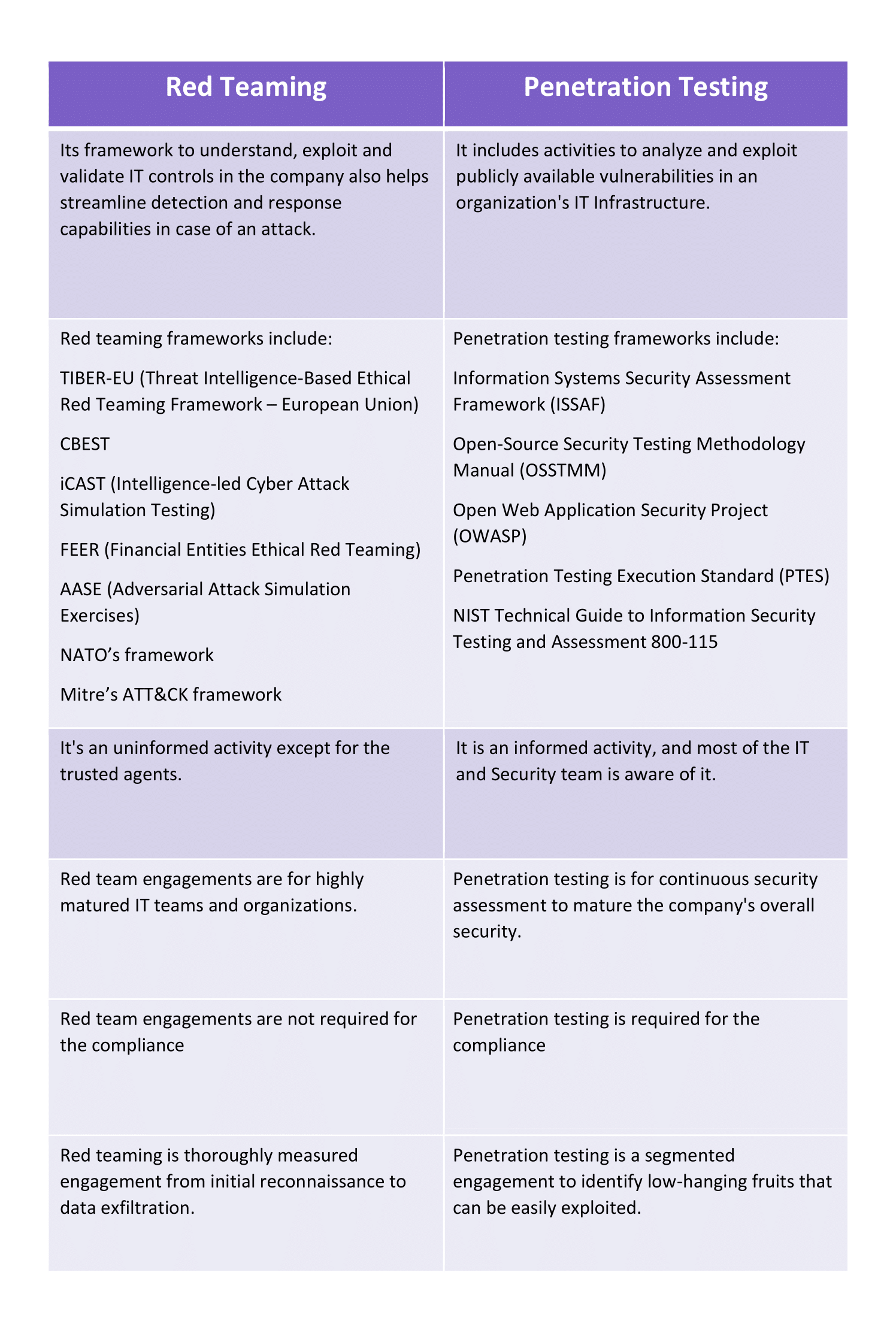
![Guide to Modern Penetration Testing [2]: Grey Box Pentesting Guide to Modern Penetration Testing [2]: Grey Box Pentesting](https://www.infopulse.com/files/images/ptes-methodology-pic-1-infopulse.jpg)