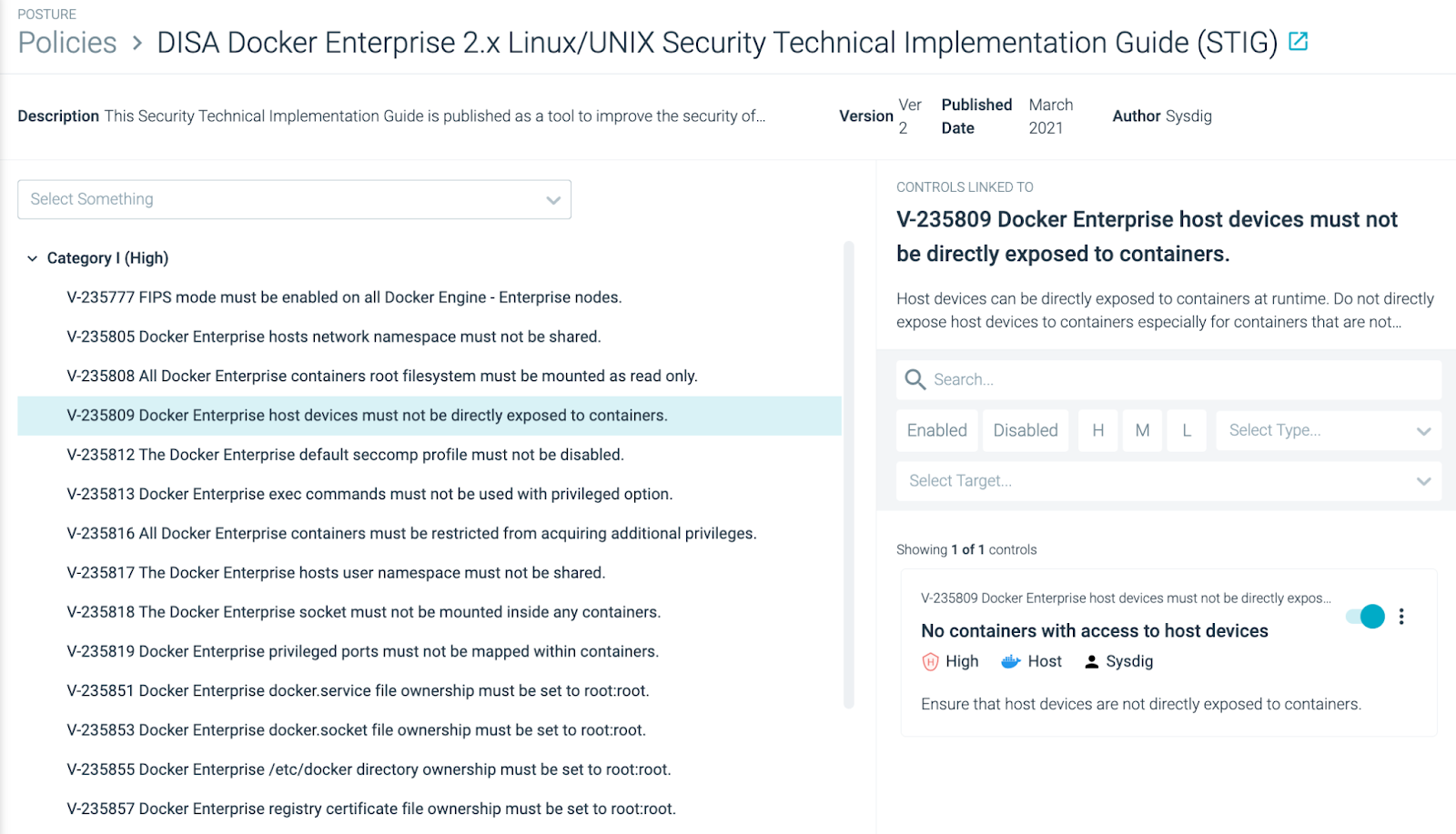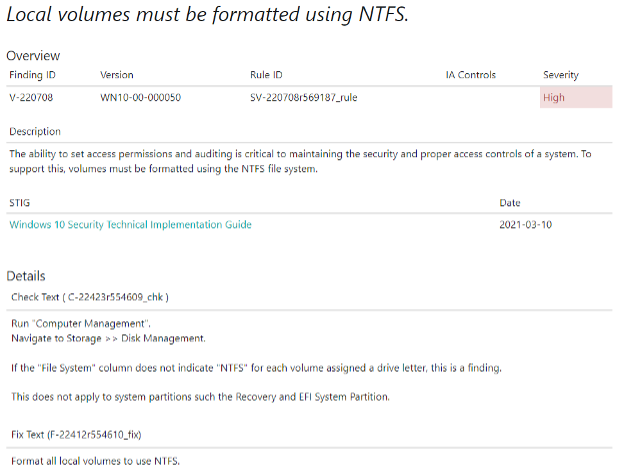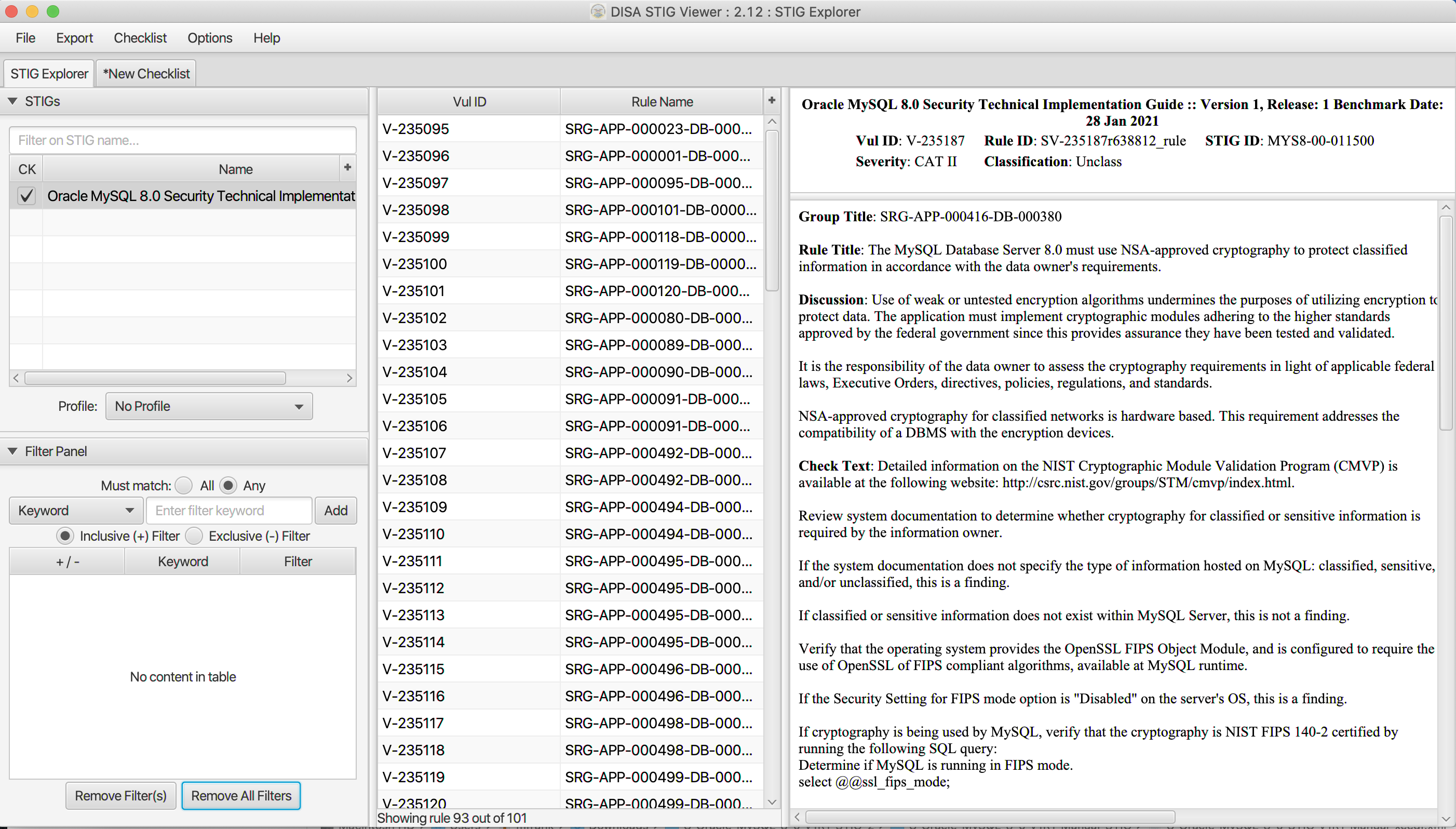
Crunchy Data Automates Security Compliance with DISA PostgreSQL Security Technical Implementation Guide

Defense Information Systems Agency al Twitter: "STIGs plays a critical role in enhancing the security posture of DOD's security systems. Latest STIG updates can be found at https://t.co/FIVoifVhJ9. https://t.co/sxW8cw6oQw" / Twitter
Defense Security Service Industrial Security Field Operations National Industrial Security Program (NISP) Authorization Office

How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems
DISA STIG (Security Technical Implementation Guides) Audit Tool for Debian - Development - Whonix Forum