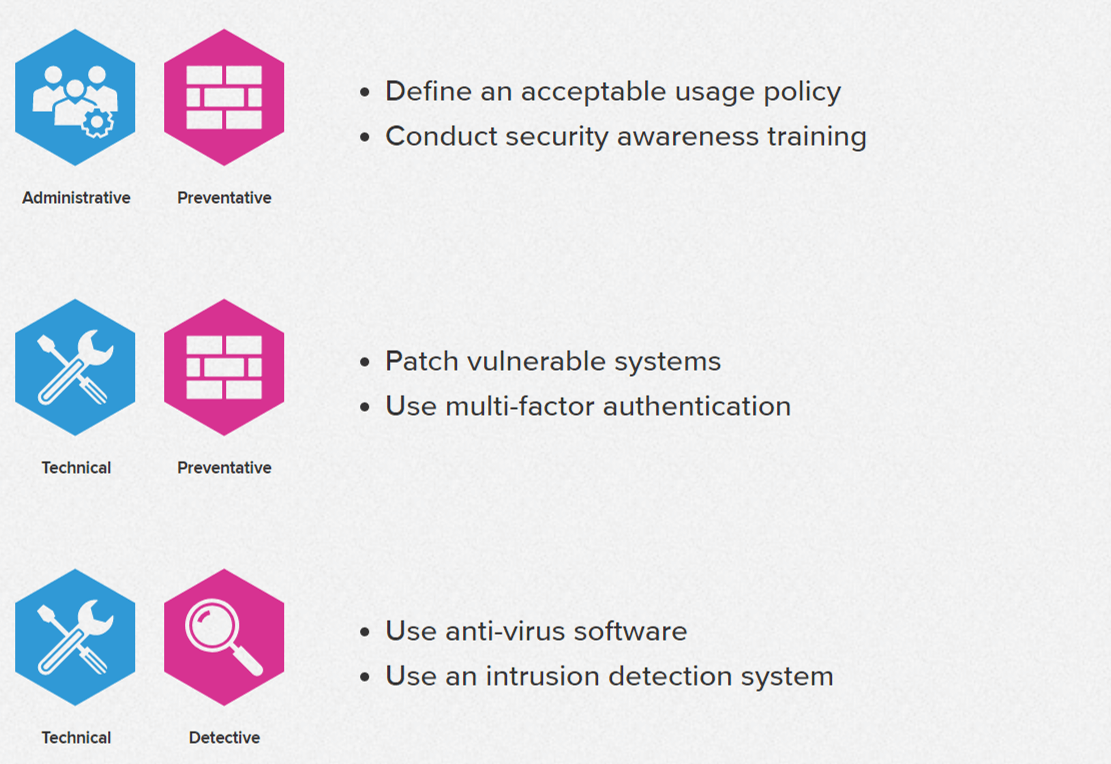
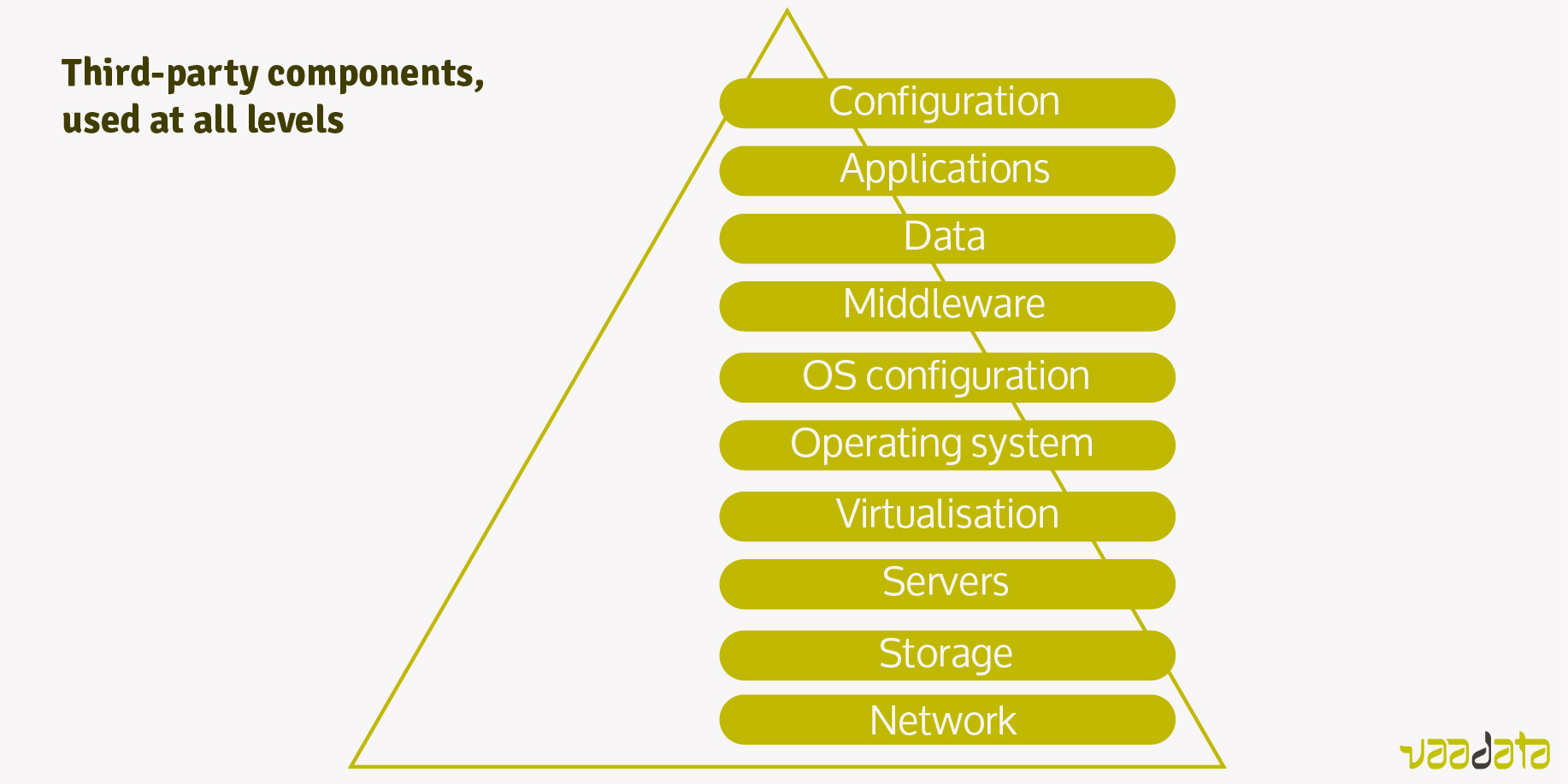
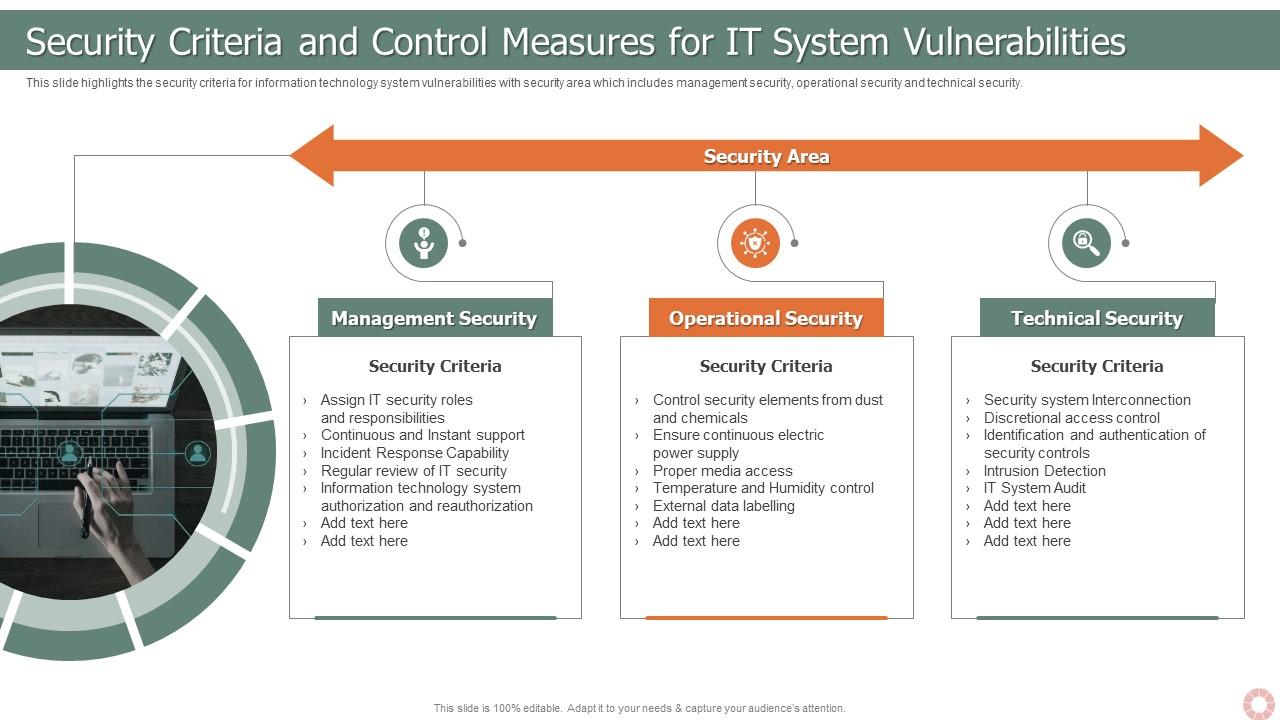
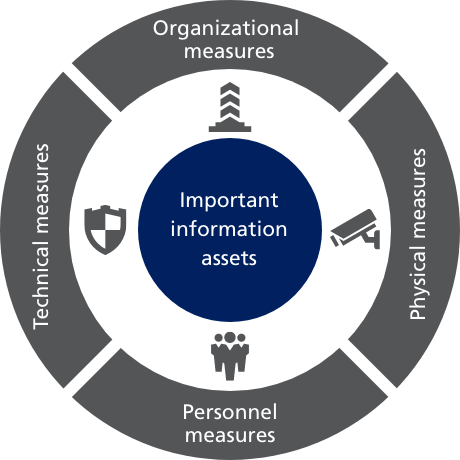
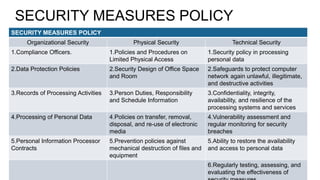
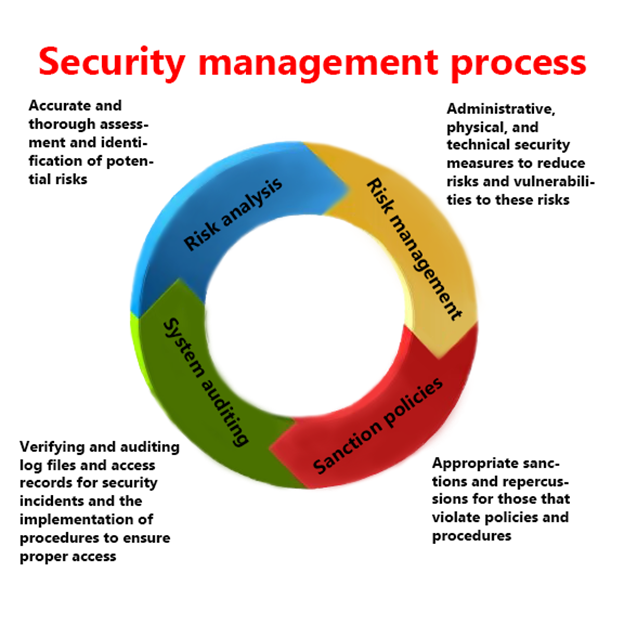
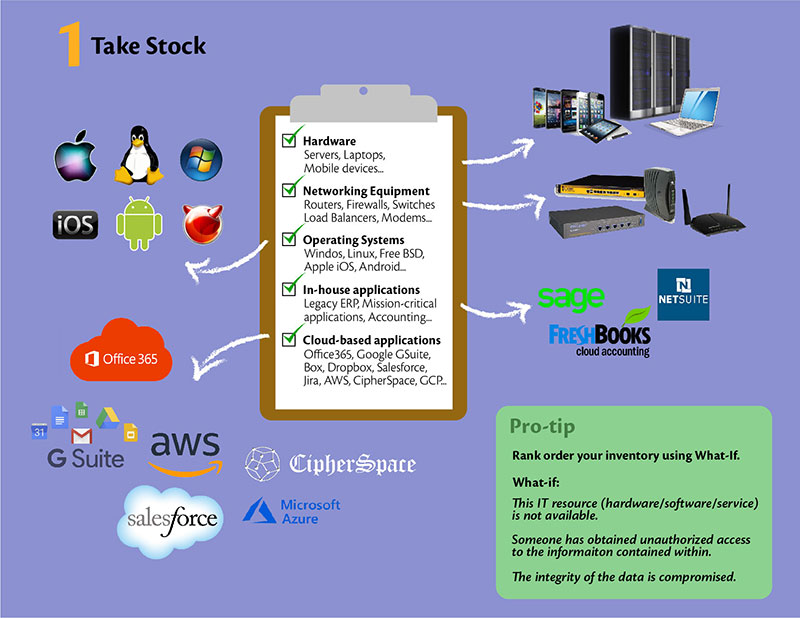
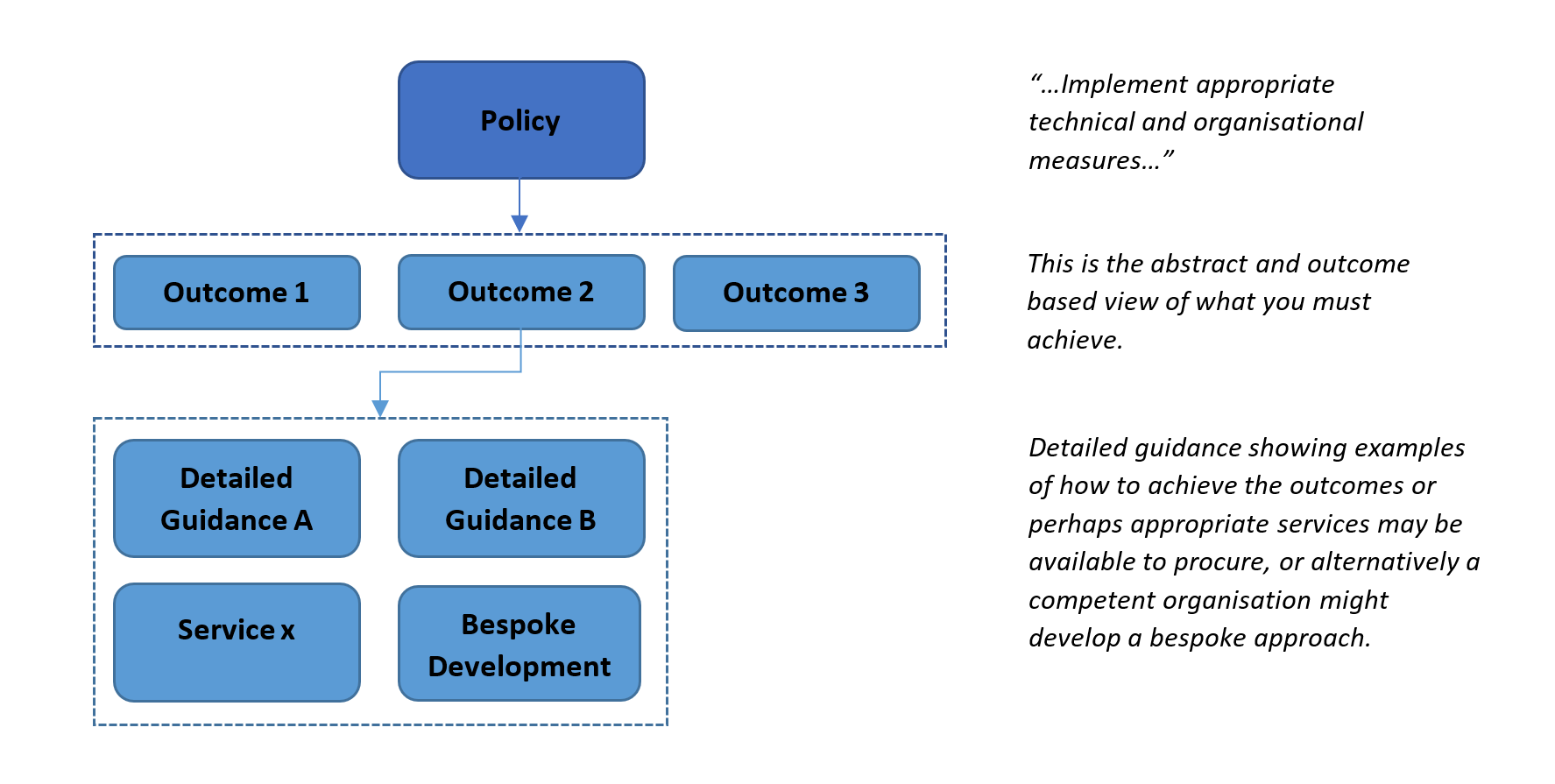
Simplified example of a security architecture with different types of... | Download Scientific Diagram

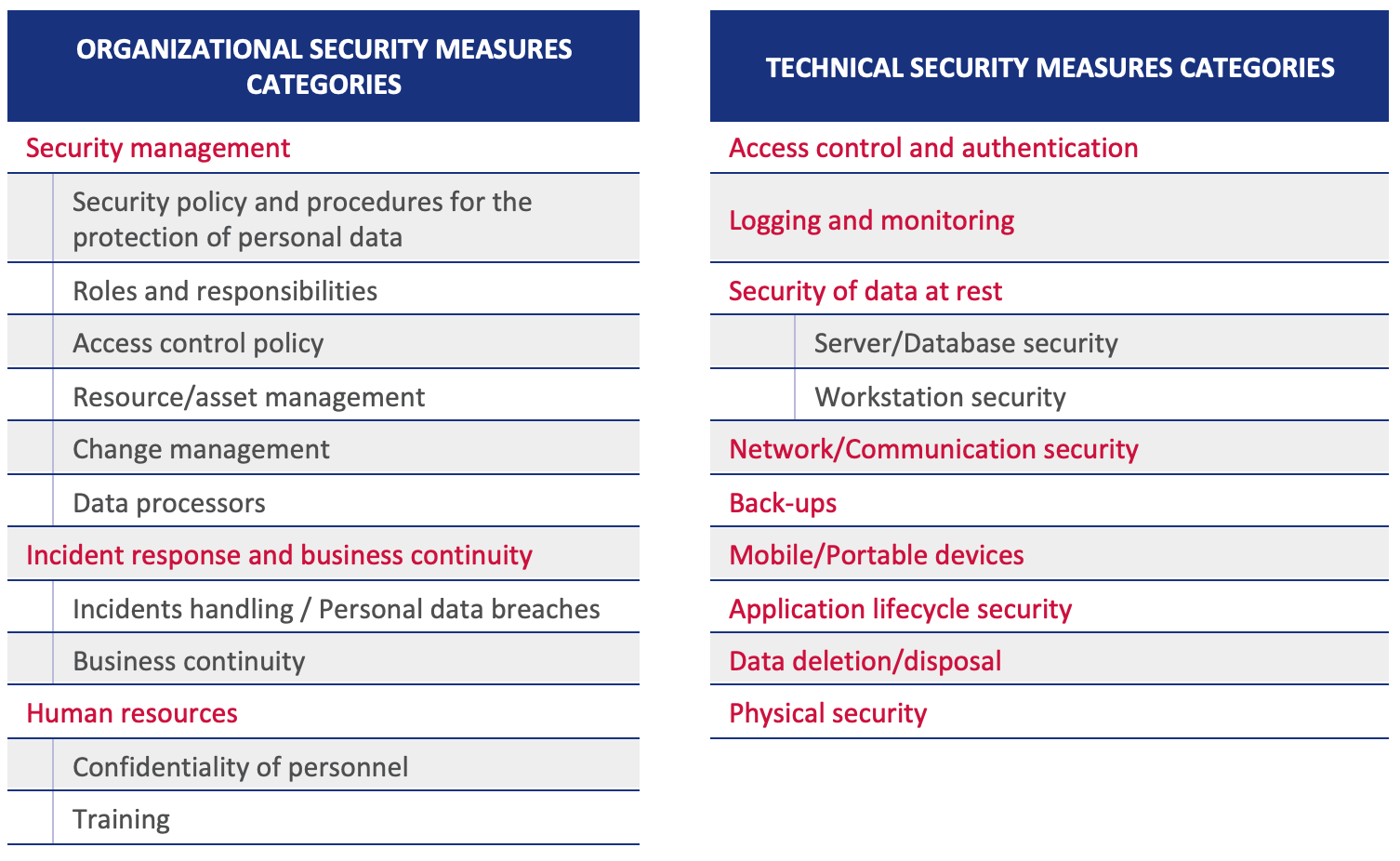
Management of Technical Security Measures: An Empirical Examination of Personality Traits and Behavioral Intentions: Social Sciences & Humanities Journal Article | IGI Global