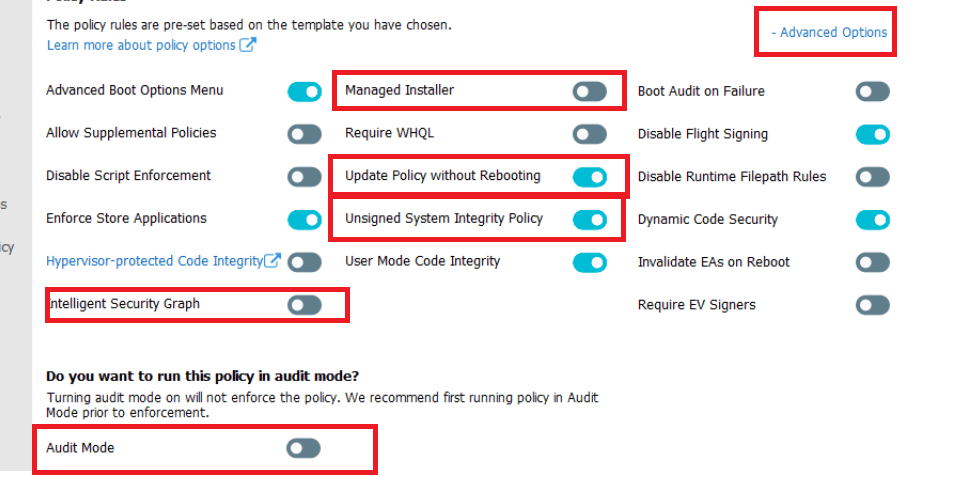
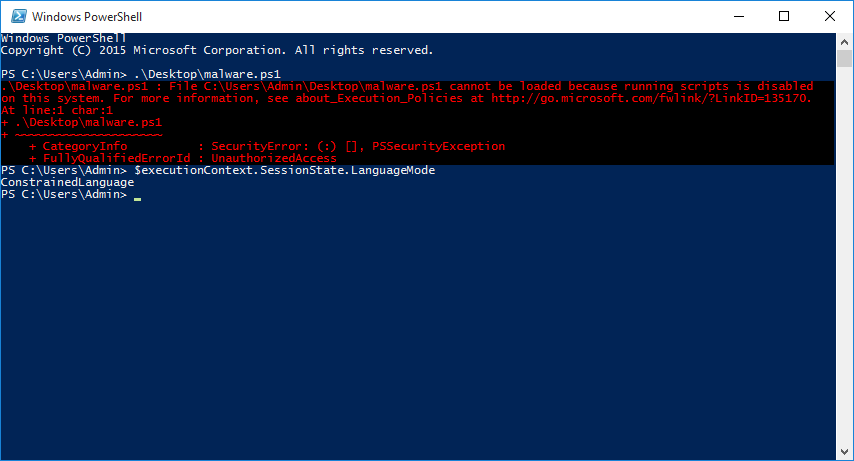
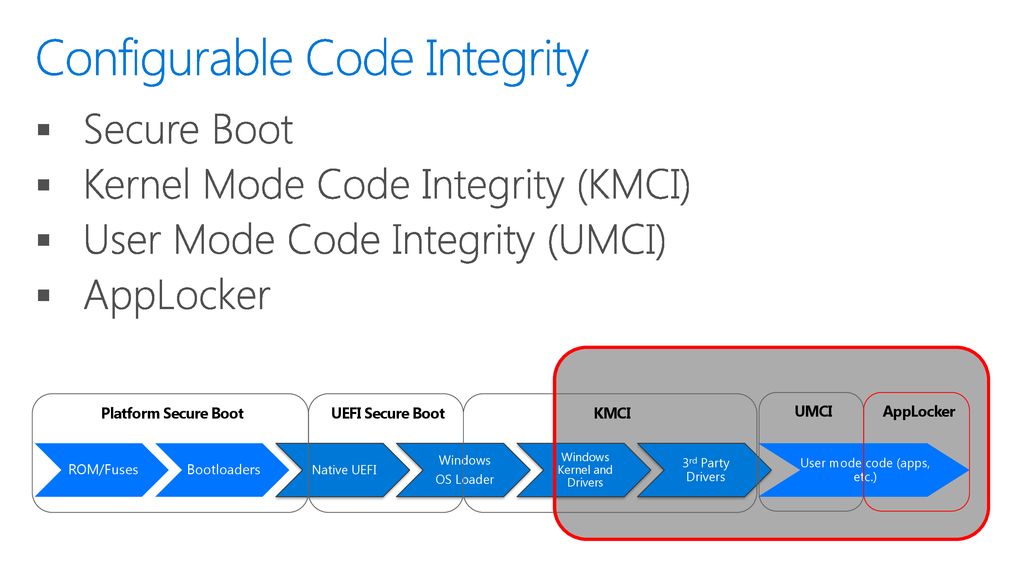
Adventures in Extremely Strict Device Guard Policy Configuration Part 1 — Device Drivers | by Matt Graeber | Posts By SpecterOps Team Members

Satoshi Tanda on Twitter: "My class at @offensive_con will discuss hiding code patches with EPTs and give away an example implementation. It is not novel, but everyone at the conf likes to

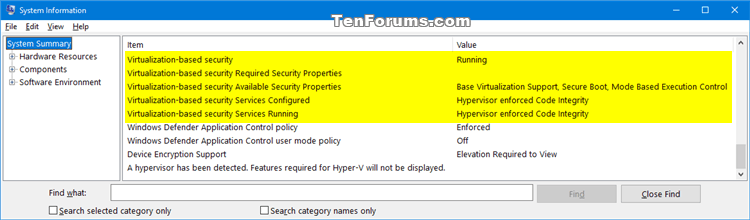
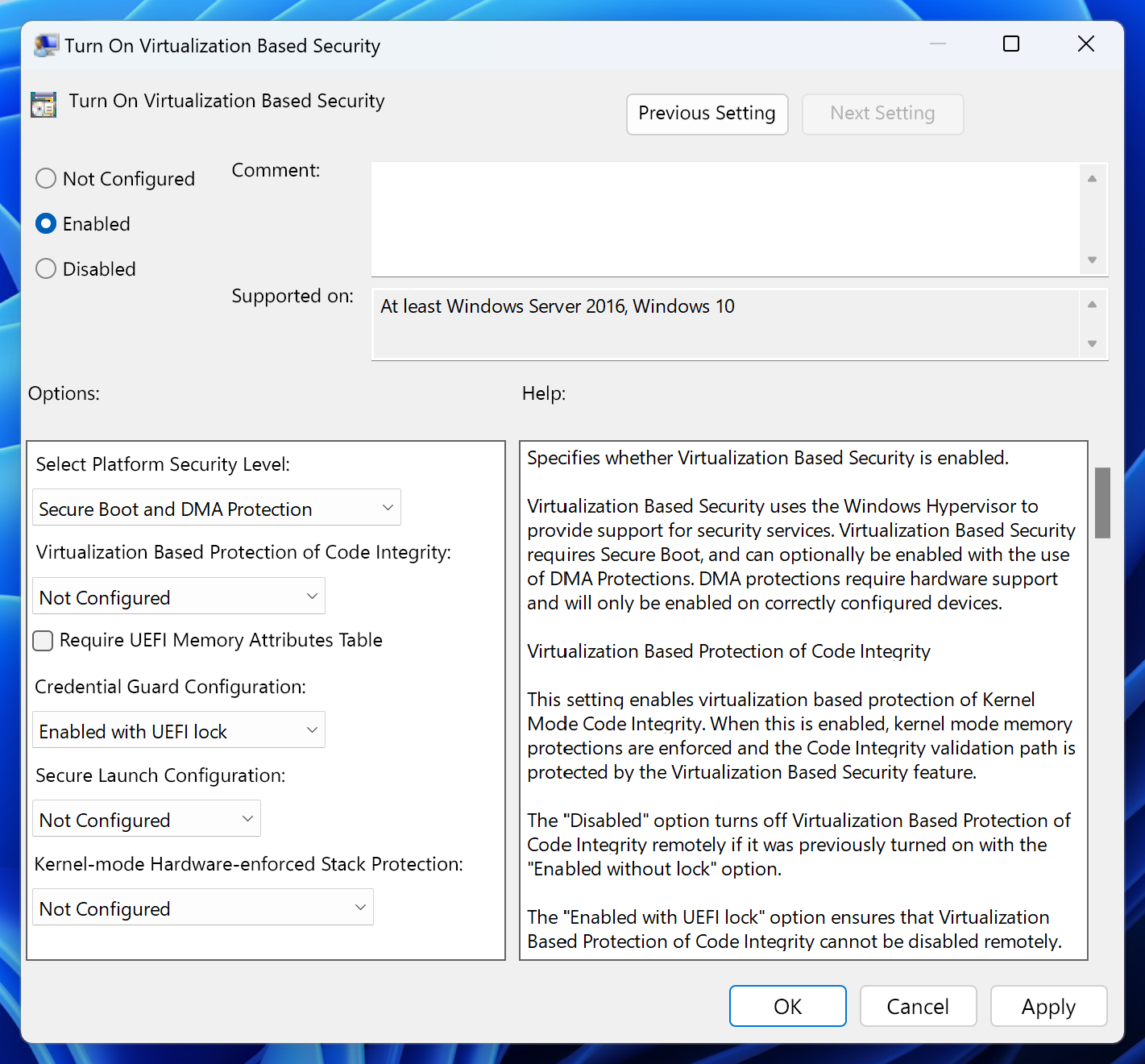
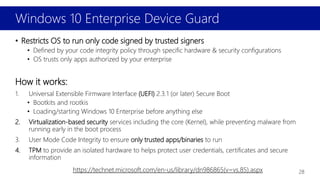
Virtualization Based Security (VBS) and Hypervisor Enforced Code Integrity (HVCI) for Olympia Users! - Microsoft Community Hub