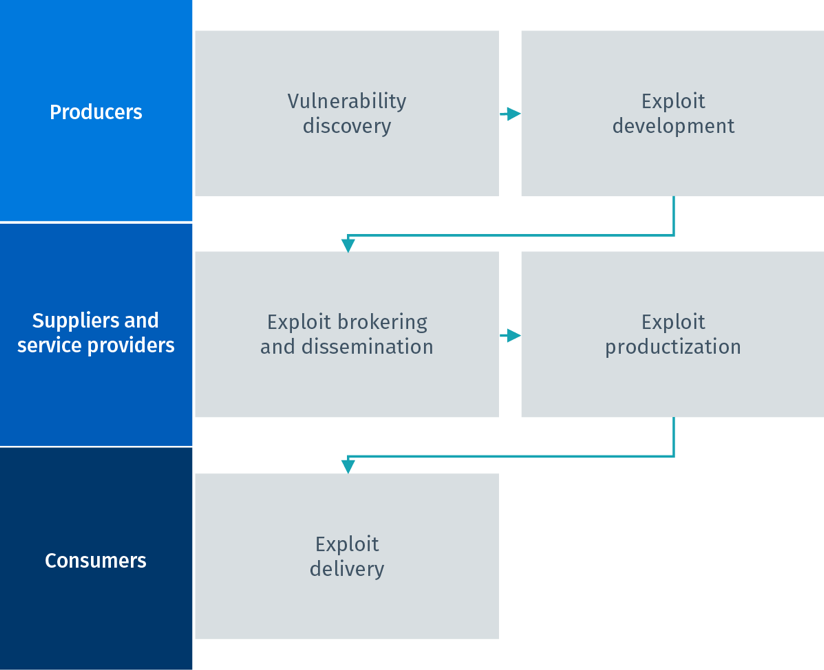
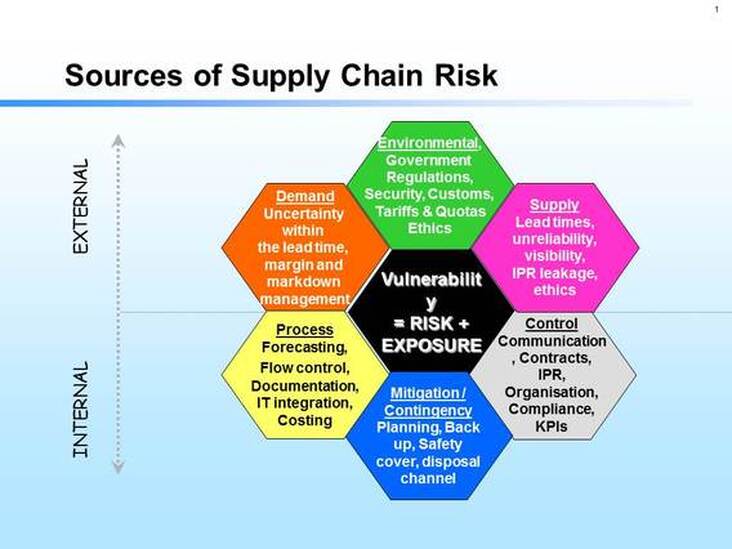
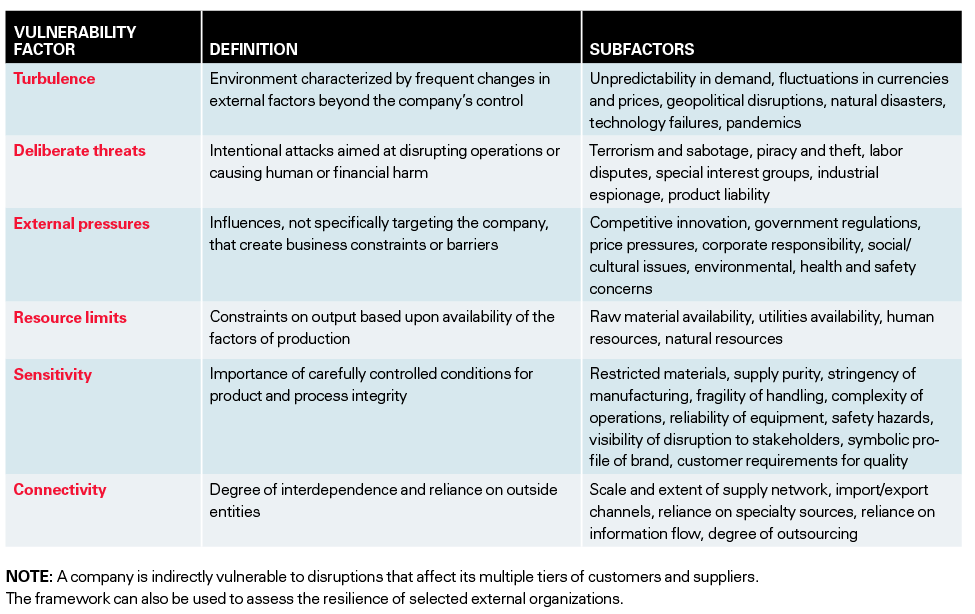
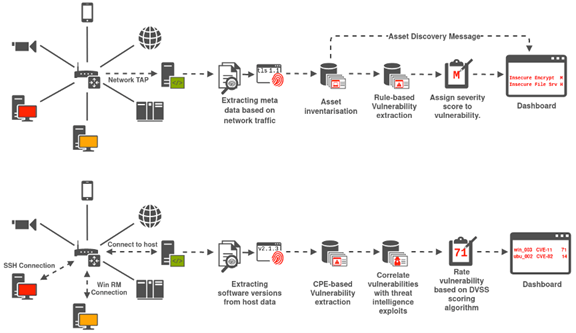
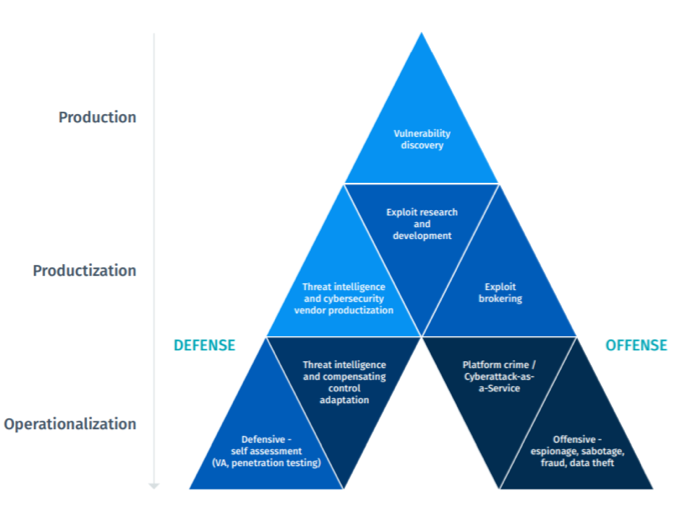
Spectrum of supply chain vulnerabilities: examples of potential disruptions | Download Scientific Diagram

A graph theory-based methodology for vulnerability assessment of supply chains using the life cycle inventory database - ScienceDirect

Supply chain vulnerability assessment: A network based visualization and clustering analysis approach - ScienceDirect
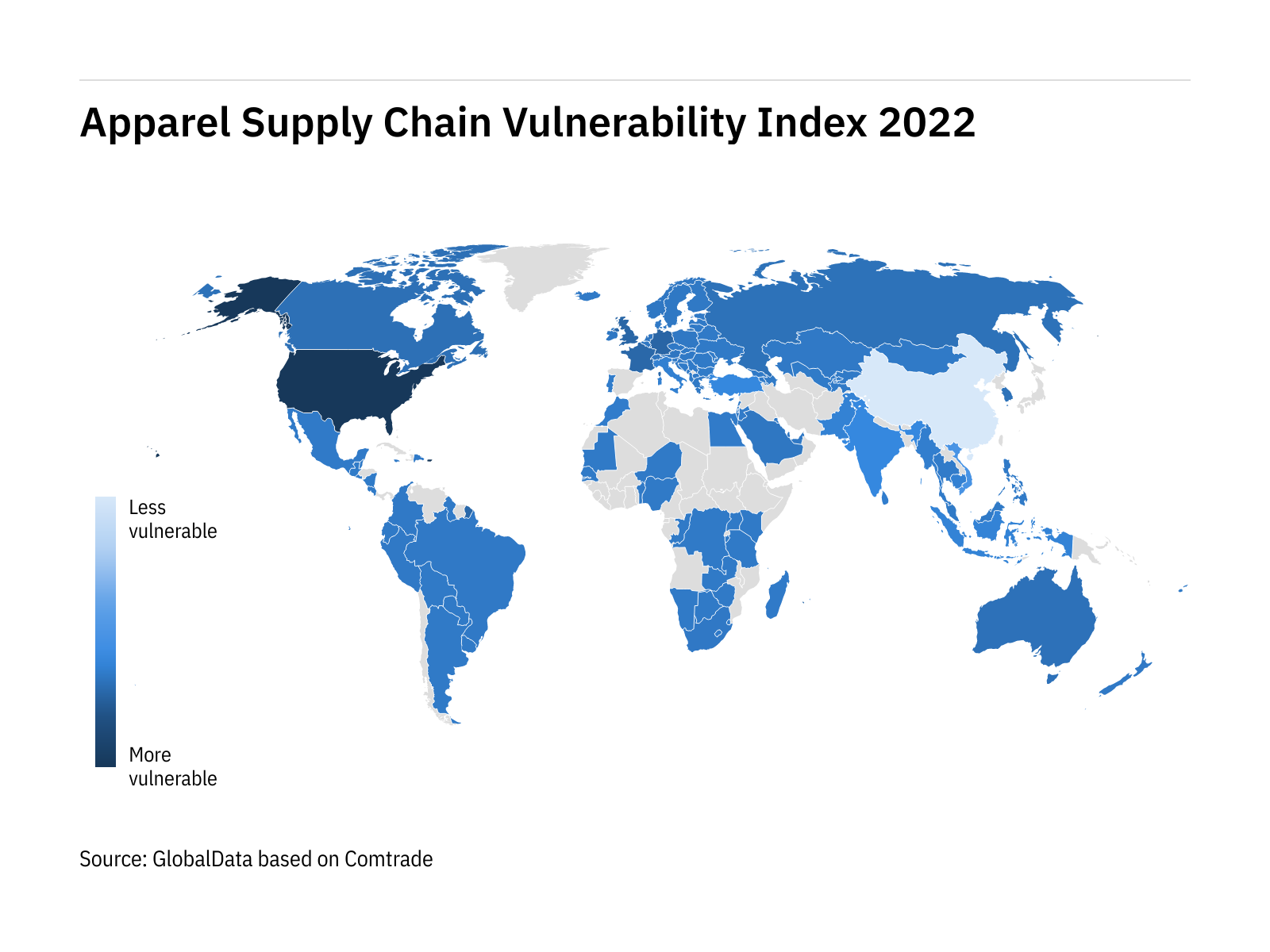


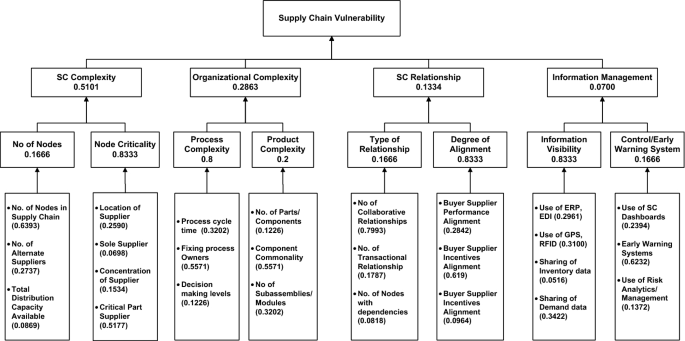



![PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c50328abeea3d9dea2146af86d1ca90996de067d/3-Figure2-1.png)