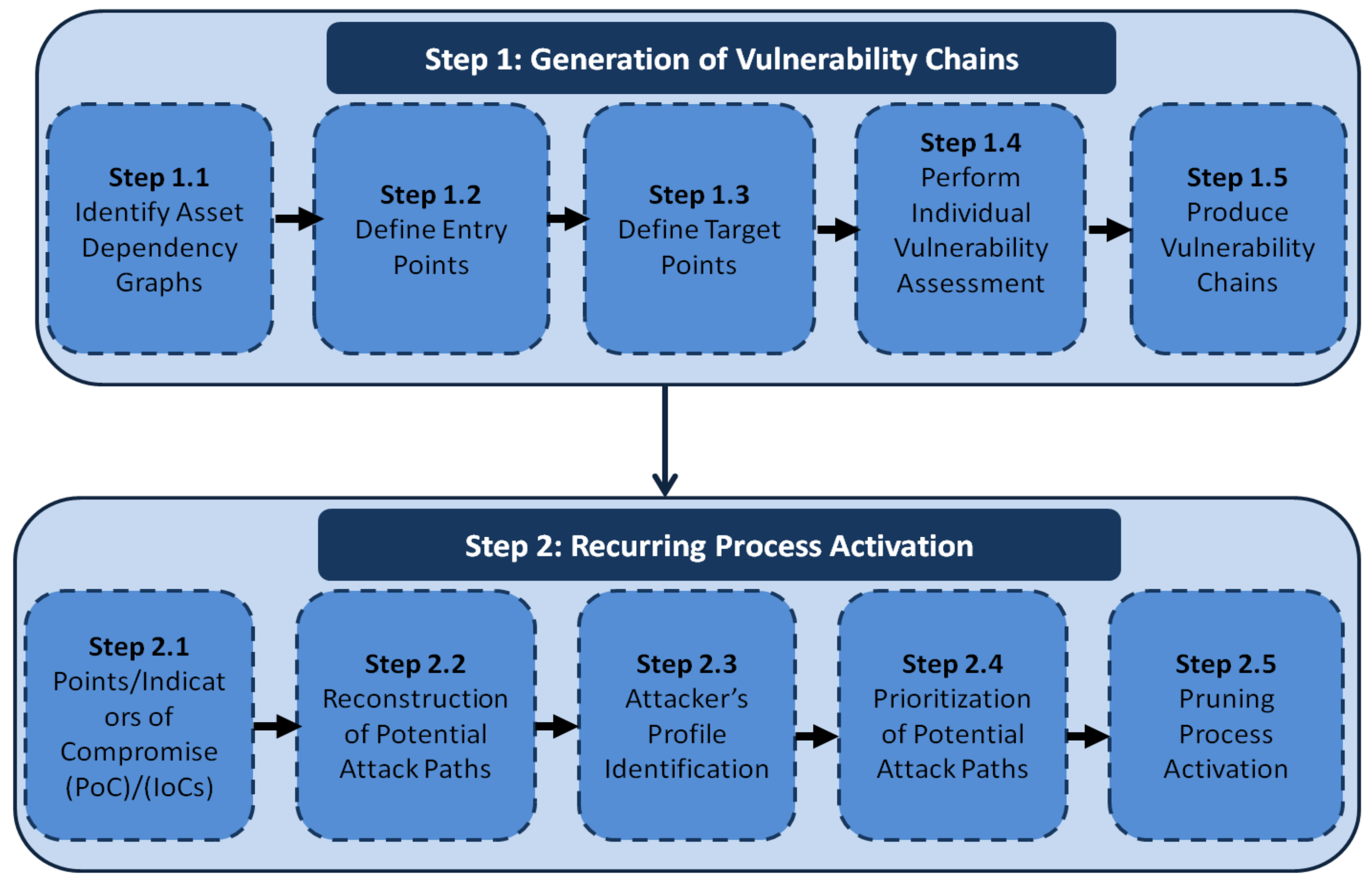
Electronics | Free Full-Text | An Attack Simulation and Evidence Chains Generation Model for Critical Information Infrastructures

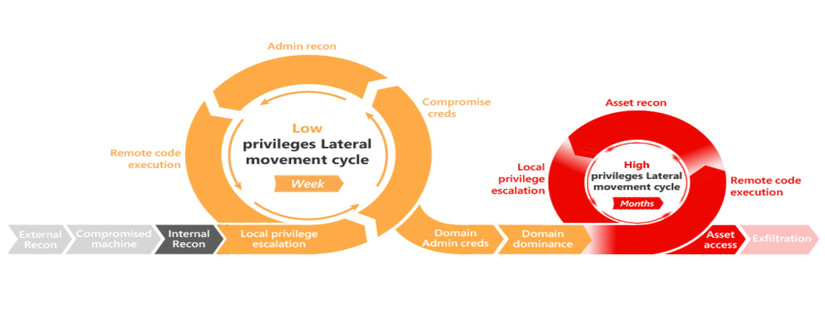
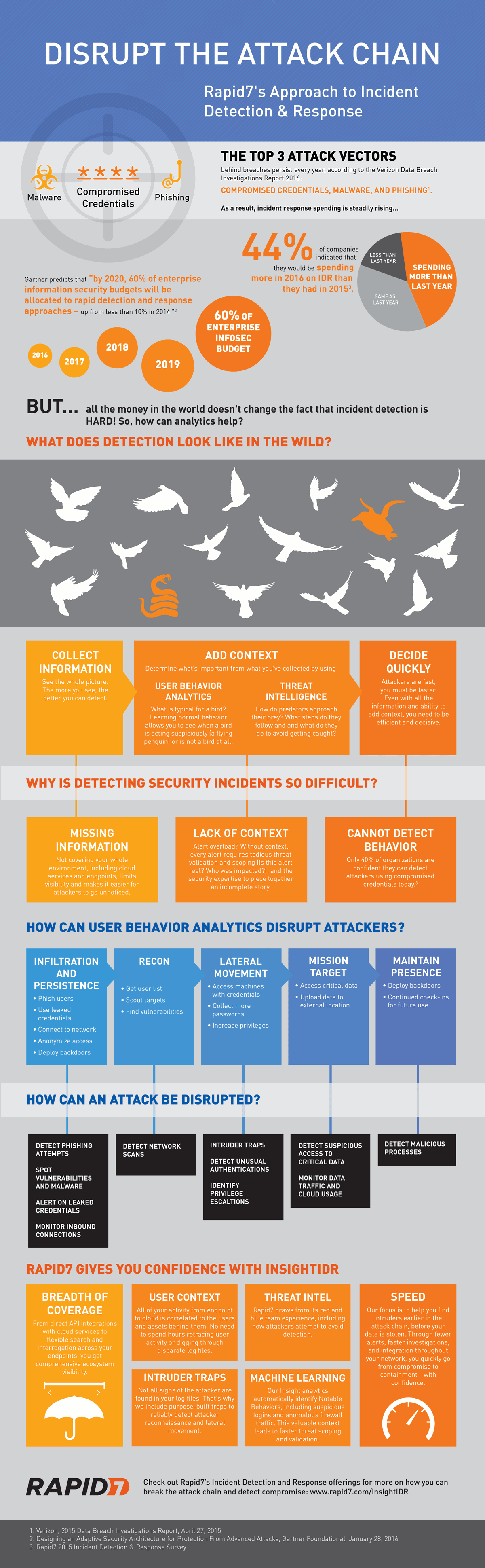
Inside Microsoft 365 Defender: Mapping attack chains from cloud to endpoint - Microsoft Security Blog

Inside Microsoft 365 Defender: Mapping attack chains from cloud to endpoint - Microsoft Security Blog