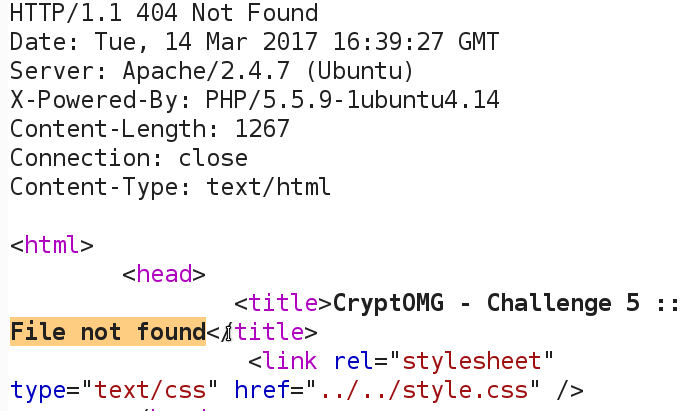
SANS Penetration Testing | Modern Web Application Penetration Testing Part 2, Hash Length Extension Attacks | SANS Institute
HashPump - Exploit Hash Length Extension Attack - Darknet - Hacking Tools, Hacker News & Cyber Security
GitHub - aabdelw1/length-extension-attack: a deeper dive into exploiting the SHA-1 hashing algorithm




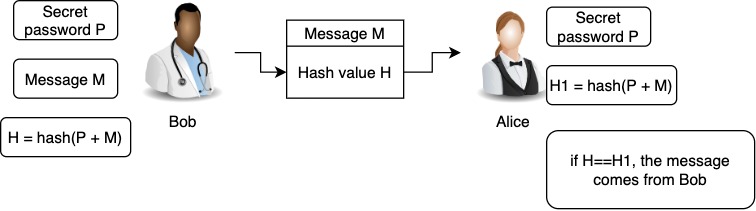






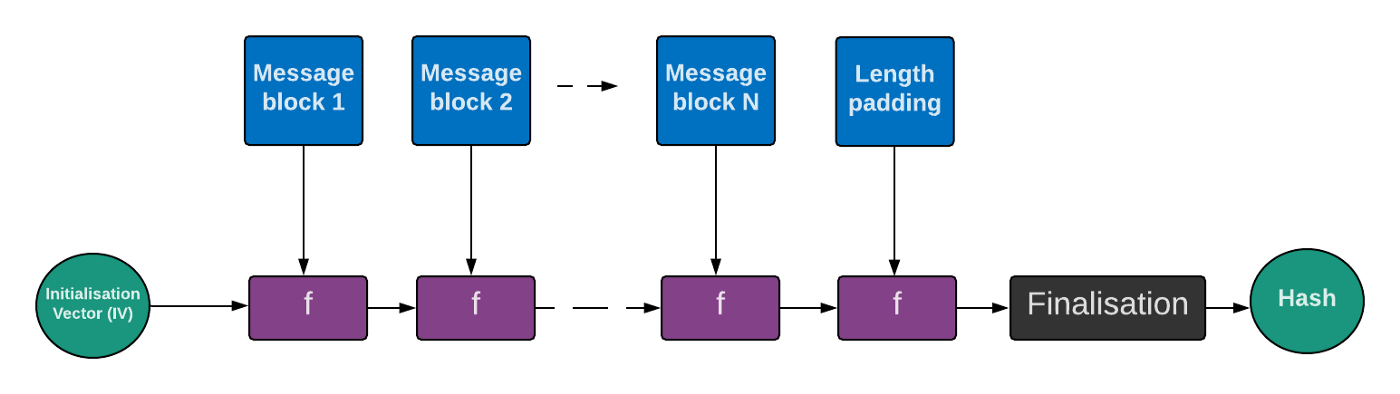


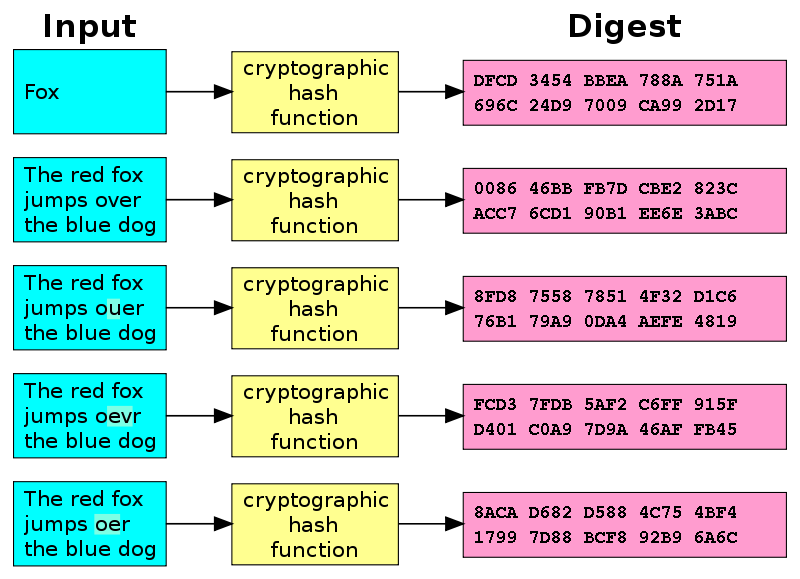
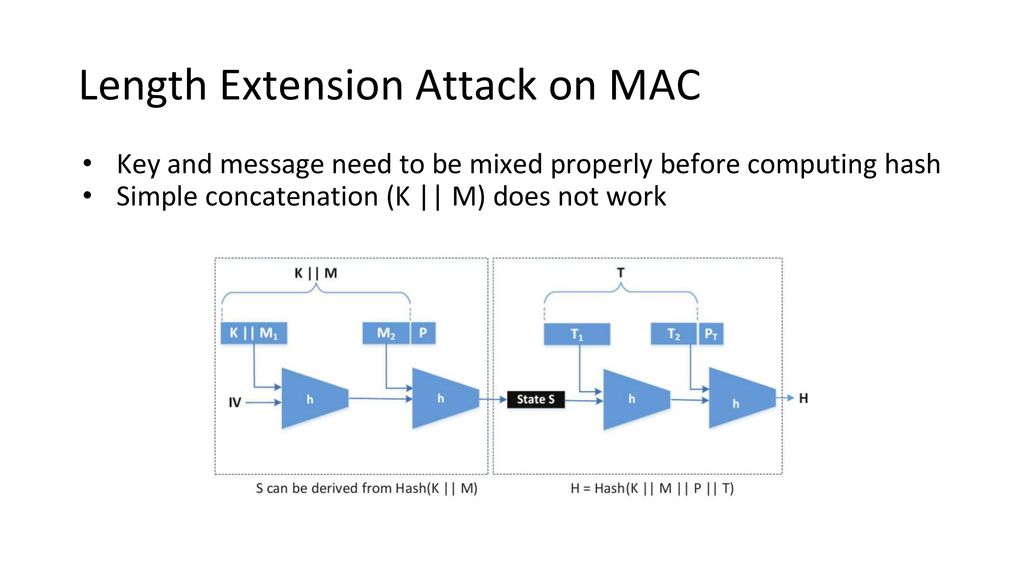



![Walking: [Crypto] Length Extension Attack Walking: [Crypto] Length Extension Attack](https://i.imgur.com/ONP0P9Y.png)