
Spectrum of supply chain vulnerabilities: examples of potential disruptions | Download Scientific Diagram
![PDF] An integrated framework for the vulnerability assessment of complex supply chain systems | Semantic Scholar PDF] An integrated framework for the vulnerability assessment of complex supply chain systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6e982ca957b129eb628c26a27b3645233a3769ed/109-Table4-5-1.png)
PDF] An integrated framework for the vulnerability assessment of complex supply chain systems | Semantic Scholar
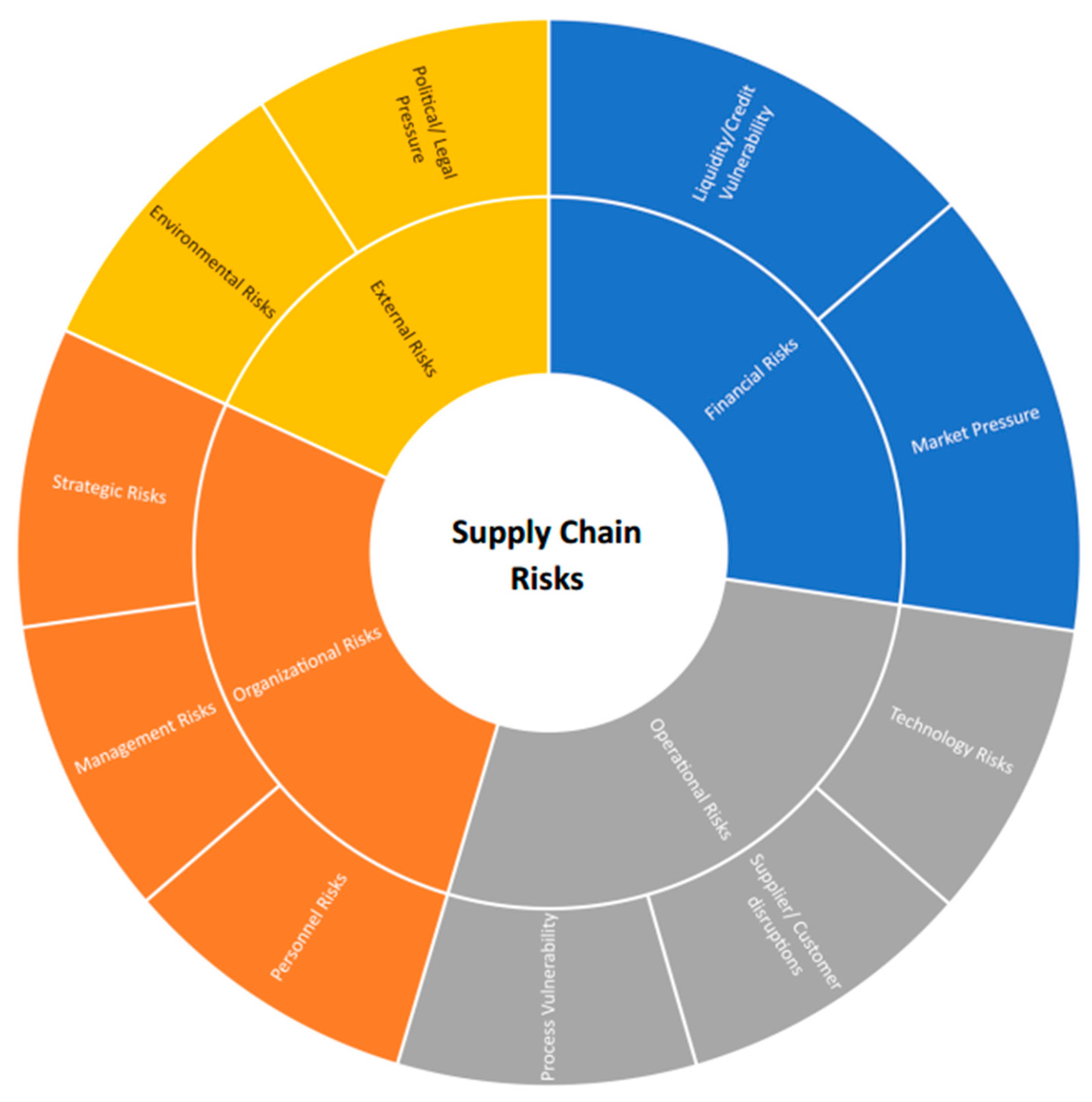
Buildings | Free Full-Text | Resilient Capabilities to Tackle Supply Chain Risks: Managing Integration Complexities in Construction Projects

Supply Chain Risk Management: Vulnerability and Resilience in Logistics : C. D. J. Waters, C. D. J. Waters: Amazon.es: Libros





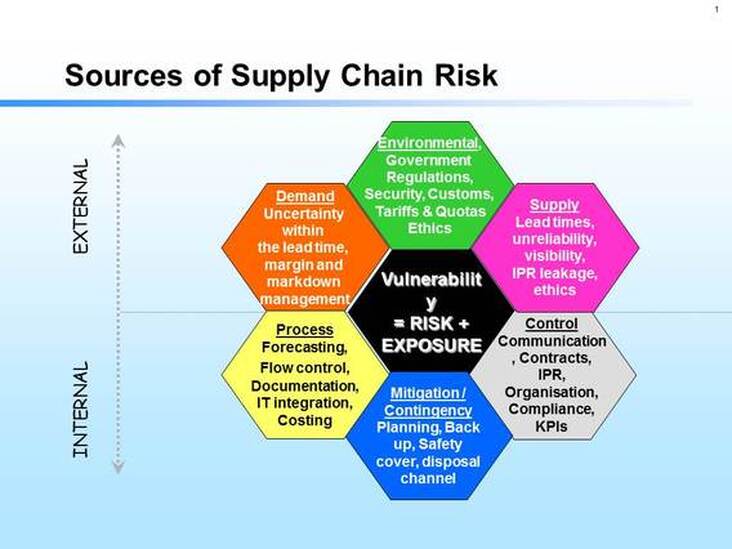

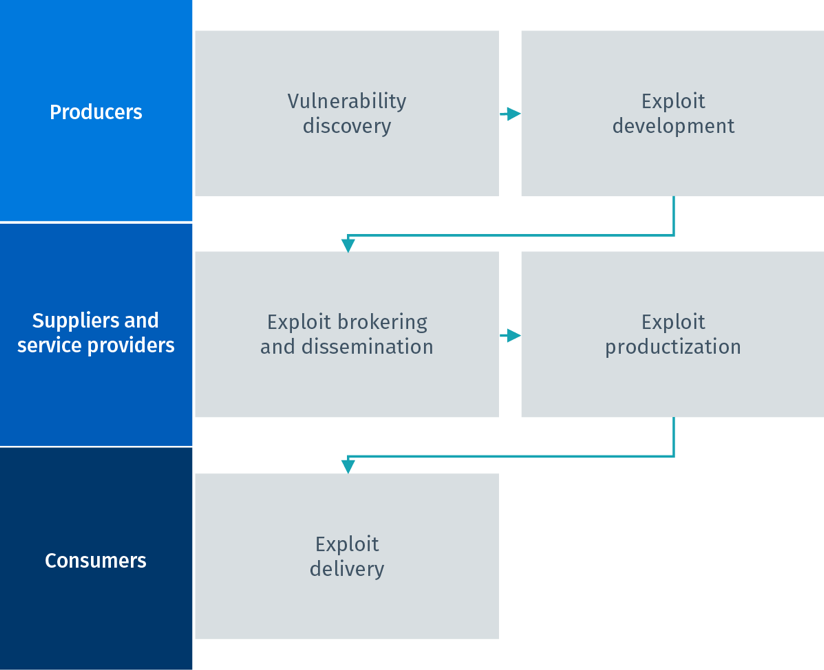
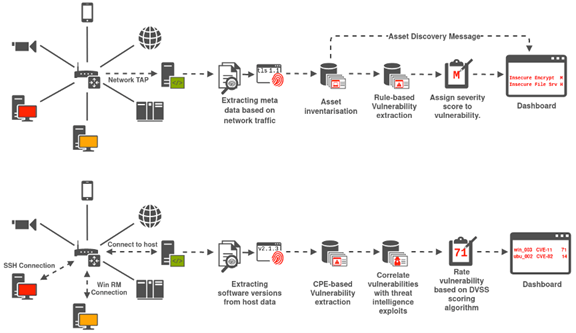


![PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c50328abeea3d9dea2146af86d1ca90996de067d/3-Figure2-1.png)