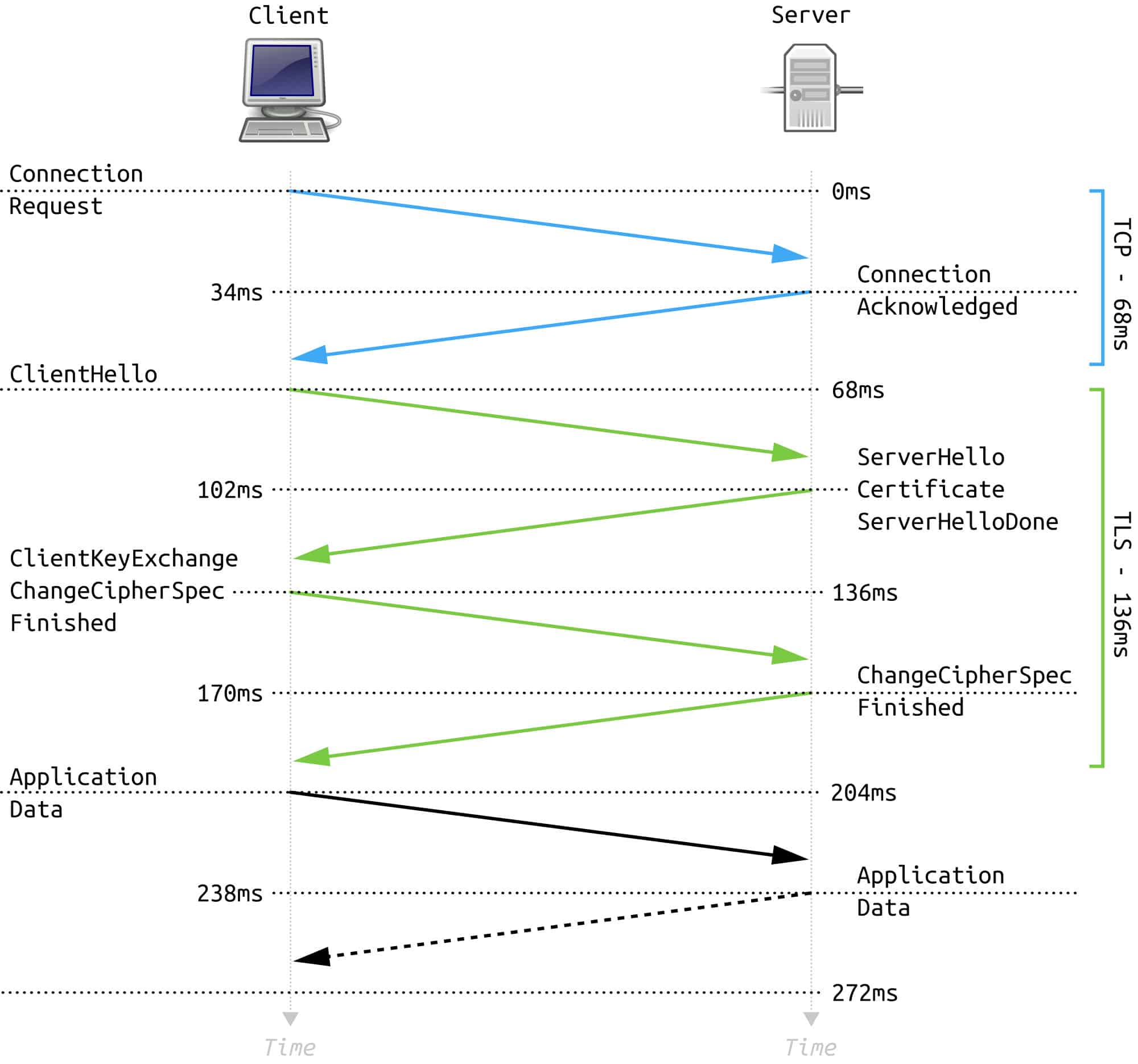
Insight Into TLS Handshake For Building Secure Communications Over The Internet. | Encryption Consulting
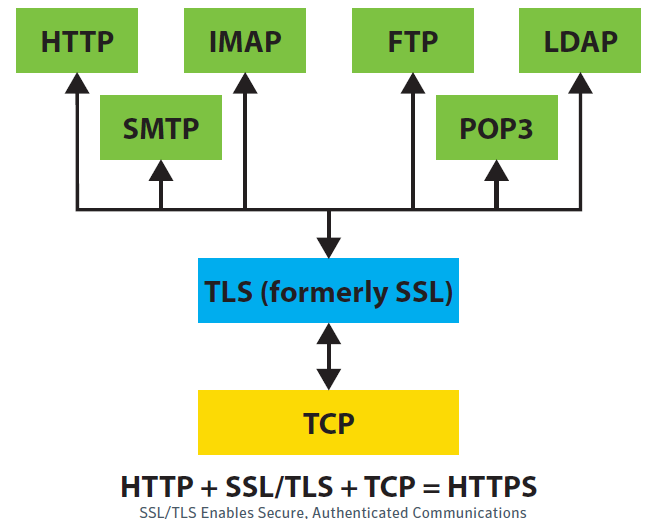
The Techniques, Technology, Applications, and Software for Decrypting TLS and SSL Encrypted Data | LIGS University

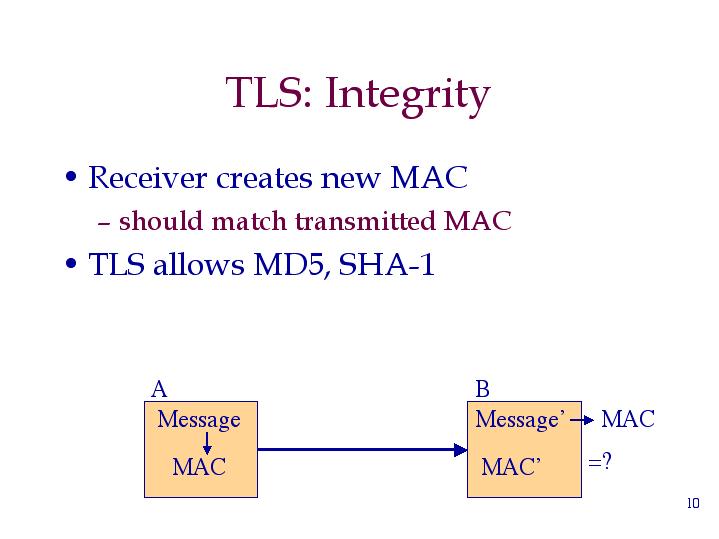
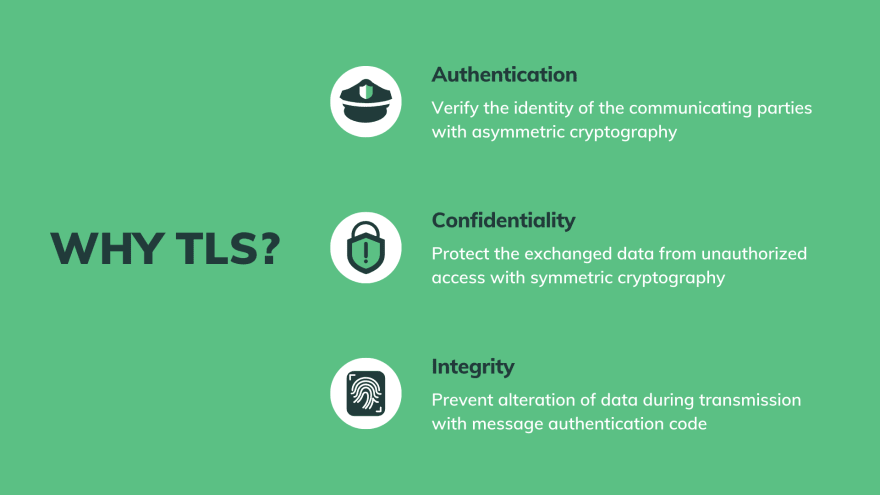
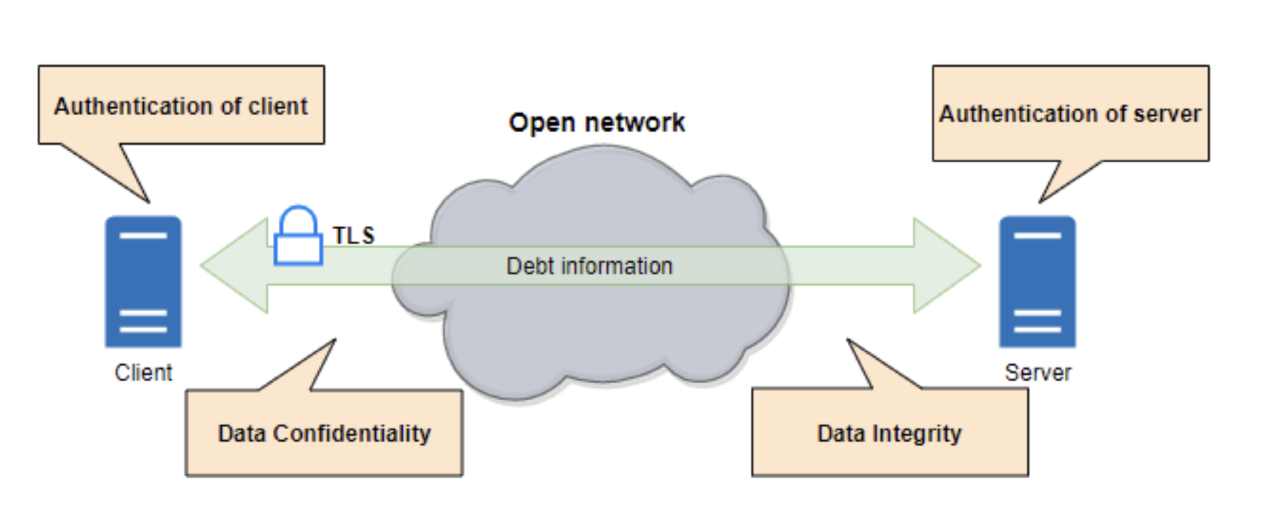
How do SSL & TLS protect your Data? - Confidentiality, Integrity, Authentication - Practical TLS - YouTube



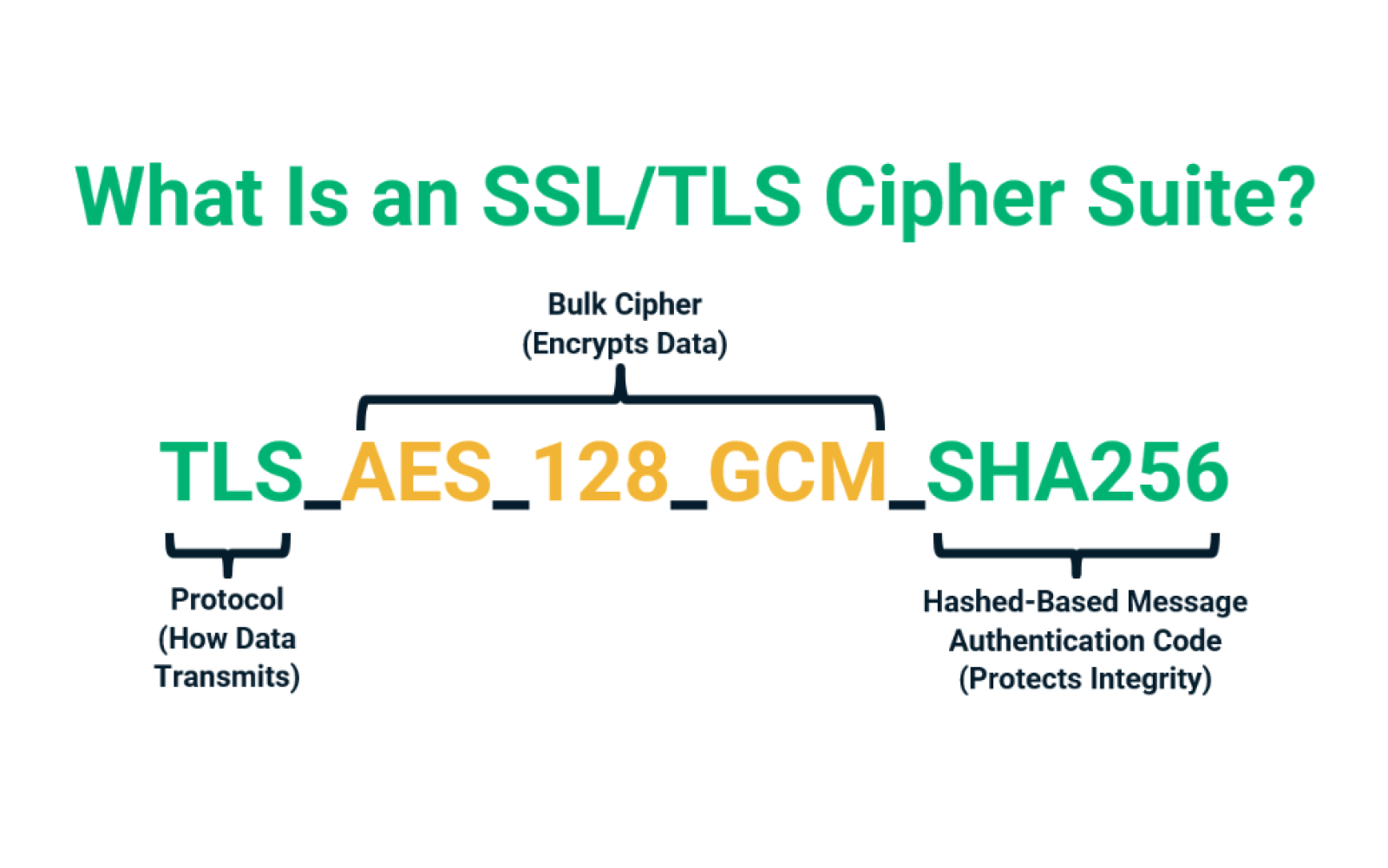


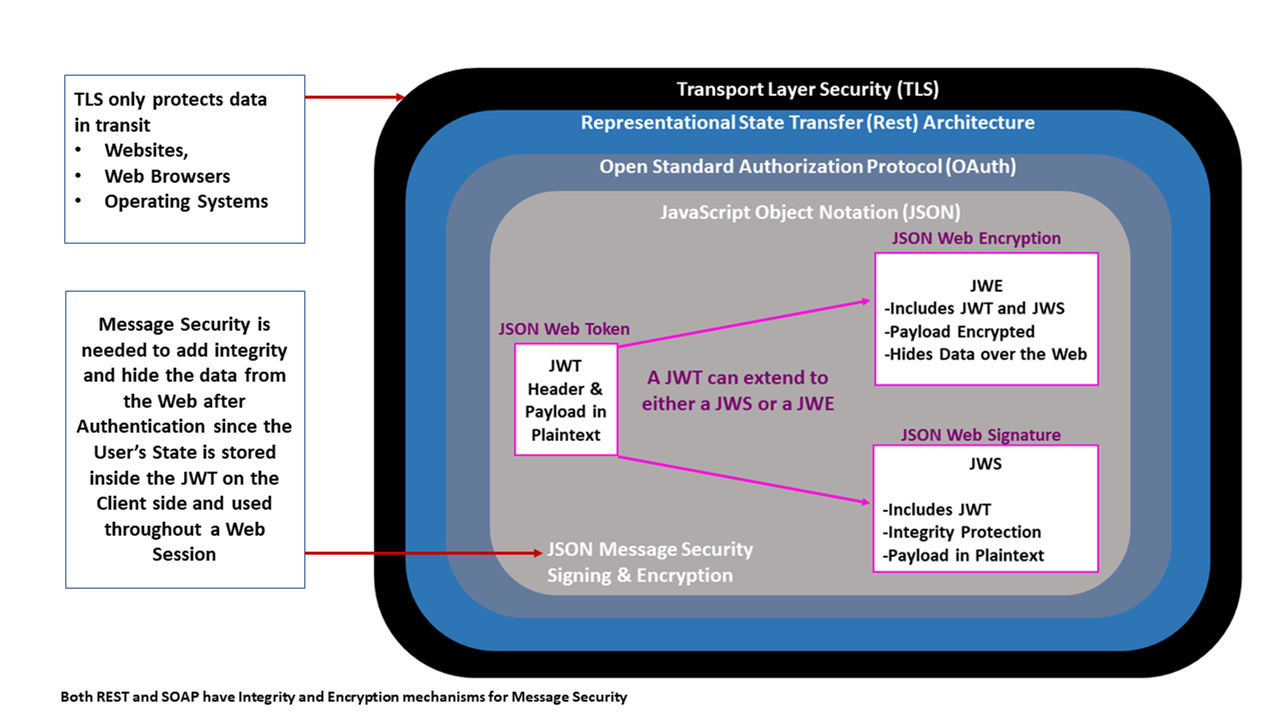


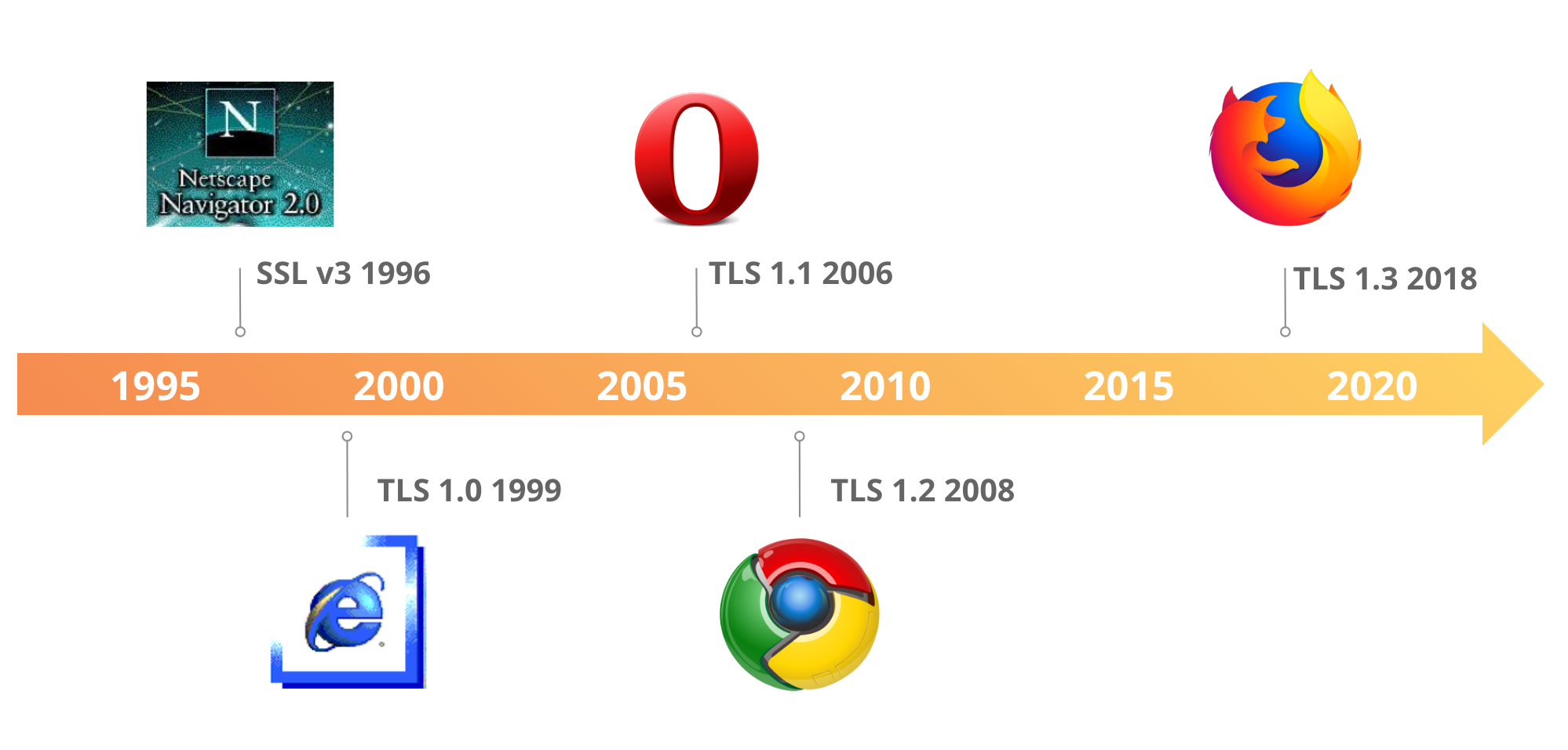
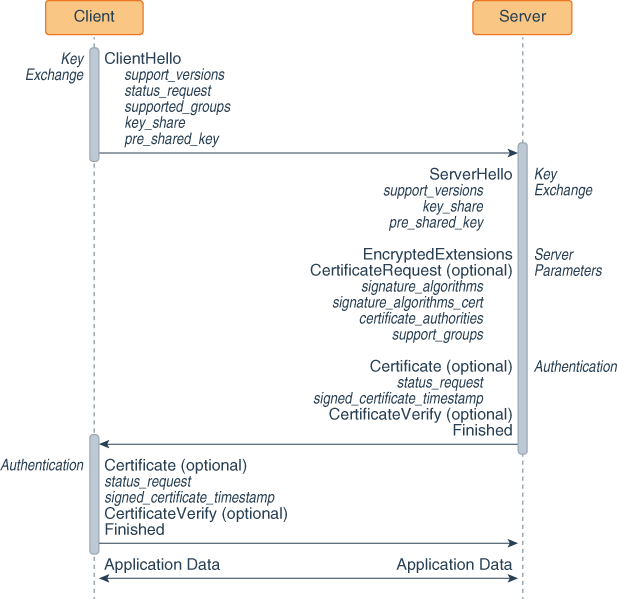
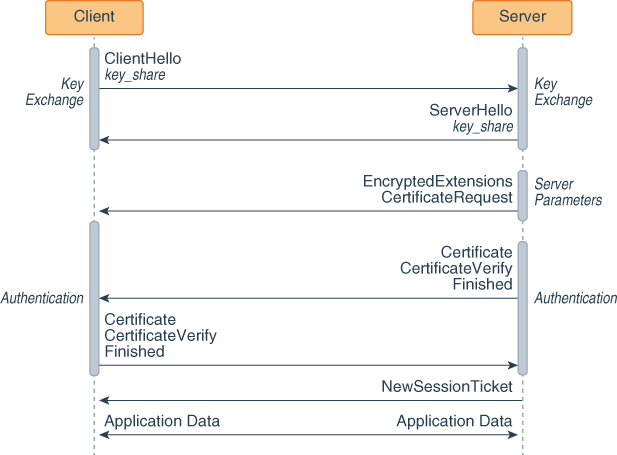
![4. Transport Layer Security (TLS) - High Performance Browser Networking [Book] 4. Transport Layer Security (TLS) - High Performance Browser Networking [Book]](https://www.oreilly.com/api/v2/epubs/9781449344757/files/assets/hpbn_0401.png)